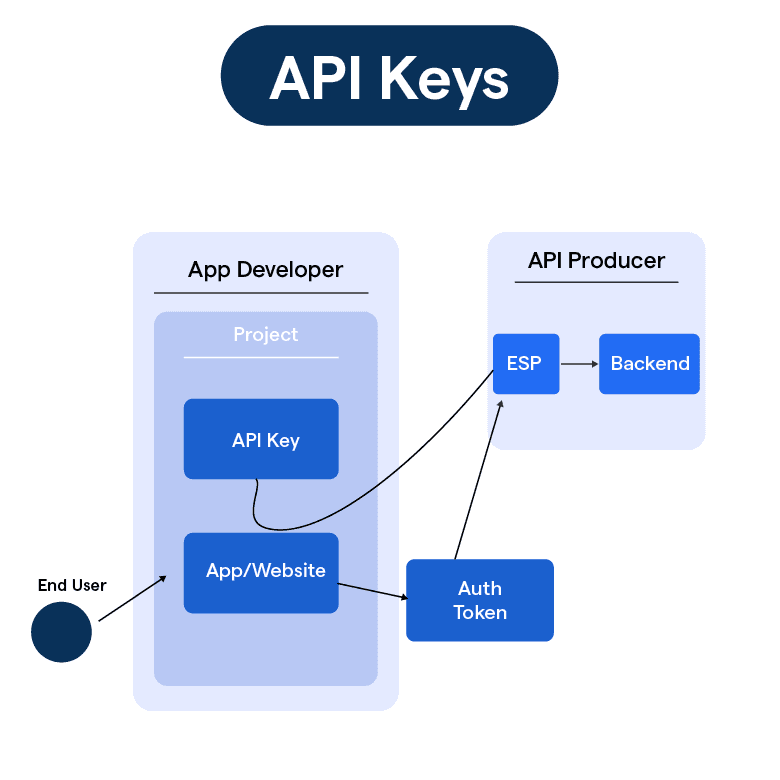
What are API Keys?
API keys are unique alphanumeric strings that authenticate and identify users, developers, or applications when interacting with a particular Application Programming Interface (API).
Why Are API Keys Necessary?
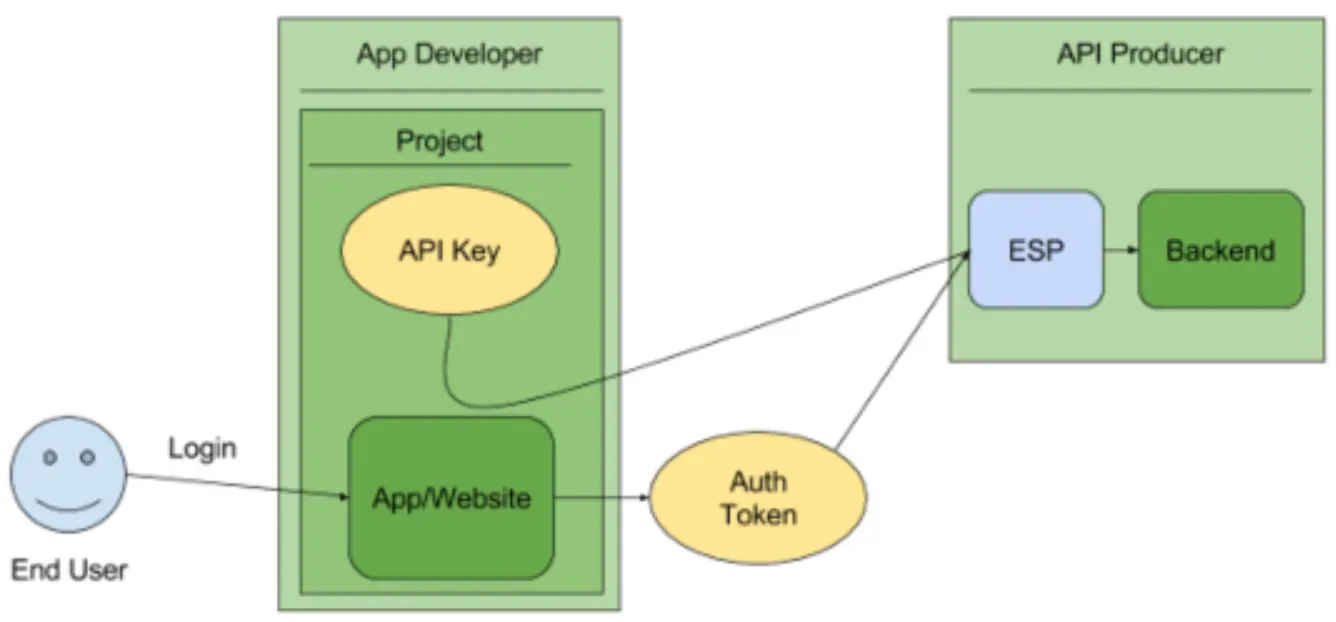
API keys serve as the access control mechanism to protect sensitive data and ensure the proper functioning of the API service. They grant permissions, restrict access to authorized users, and safeguard the server and the users' data.
Usage Benefits
API keys are not only fundamental for security but also help service providers monitor and analyze the usage patterns of the APIs. This insight helps them improve the functionality, manage resources efficiently, and detect abuse or potential threats.
API Key Implementation: How Providers Create and Distribute Keys
Now that we understand what API keys are, let's explore the process of implementing them from the provider's perspective.
Key Generation
Service providers generate API keys using cryptographic methods, ensuring that a unique and hard-to-guess string is created for each user or application.
Distribution and Usage
API keys are typically shared with users or developers during the registration or onboarding process upon the creation of an account with the service provider. Users then include these API keys within their applications or code to authenticate and access the API.
Key Management
API key management involves creating, organizing, and revoking keys as required. Proper management of API keys includes monitoring key usage, ensuring key expiry, and occasionally rotating keys for enhanced security.
Integrating with User Authentication
API keys are sometimes paired with other user authentication methods, such as OAuth or JWT tokens, to complement and strengthen the overall security.
Popular Formats and Storage Processes
API keys come in various formats, and it's essential to understand how to store and use them securely.
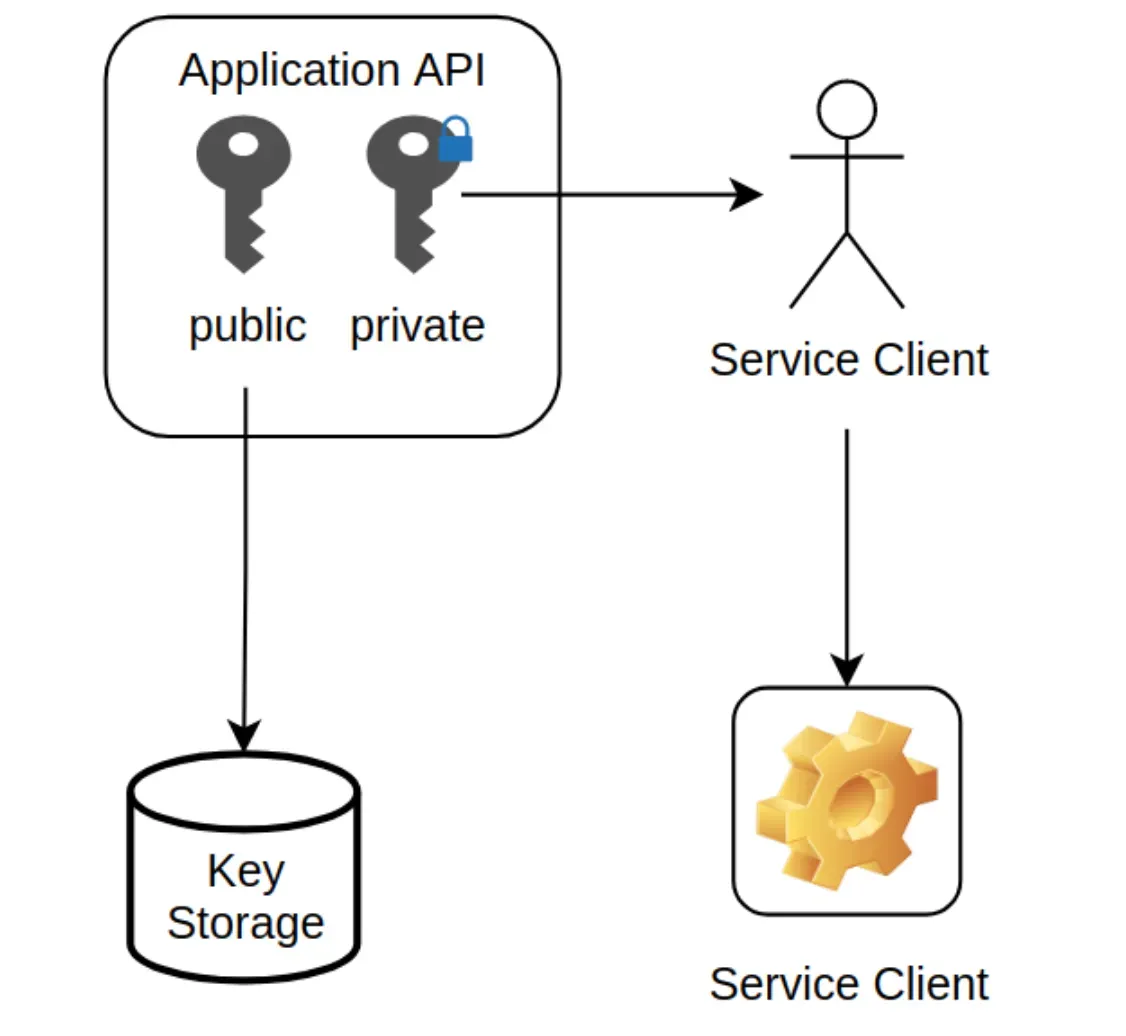
Formats of API Keys
API keys may be simple strings or more advanced structures, such as JSON Web Tokens (JWT). The format depends on the API provider's preference and the level of complexity required for security.
Storing API Keys Securely
Keeping API keys secure is crucial. They should be stored in a secure location, such as within environment variables, encrypted files, or dedicated secret management systems on the user's side.
Passing API Keys in Requests
There are multiple ways to pass API keys in requests: URL query parameters, HTTP headers, or within the request payload. It is typically recommended to include them in HTTP headers to avoid exposing them in logs or browser histories accidentally.
Key Rotation
Key rotation involves periodically changing the API keys to enforce best security practices. This process reduces the risk of misuse and identifies unused or compromised keys.
Limitations and Potential Pitfalls
API keys are a vital part of API usage, but they're not without limitations and challenges.
Security Risks
If an API key is not handled securely, it can lead to unauthorized access, data breaches, or unauthorized use of the API. Careful handling of API keys and secure management practices must be followed.
Scalability Challenges
API key authentication can be challenging when it comes to scalability as APIs grow in complexity and usage. Integrating addon mechanisms like OAuth and JWT tokens, or using other forms of authentication, might be more suitable in such cases.
Credentials Leaks
API key leaks are a significant concern. If the API keys are exposed through code repositories, unsecured storage, or poor implementation, attackers may gain unauthorized access to sensitive data and systems.
Dependence on Provider Security
User security is also contingent on the API provider's security. An API provider's compromise can lead to potential vulnerabilities for users who implement the API keys.
Best Practices for Handling API Keys

To avoid pitfalls, follow these best practices for handling and managing API keys.
Don't Hardcode API Keys
Avoid hardcoding API keys within your source code. This measure prevents potential exposure if your source code is shared or hacked. Store the keys securely in dedicated secret management systems or encrypted files.
Monitor Usage
Keep track of API key usage to detect anomalies, unauthorized access, or signs of misuse. Frequently audit and analyze logs to maintain optimal security and performance.
Implement Key Rotation
Periodically change your API keys to minimize the risk of unauthorized access from leaked or outdated keys. Integrate an automated rotation process to replace API keys regularly.
Limit Controls and Permissions
Not all API keys need access to the entire system. Set limits to the controls and permissions an API key can access to minimize potential damage in case of unauthorized access.
Notable Examples of API Key Systems
Several well-known service providers and platforms implement API keys for authentication purposes. Here's a look at a few examples:
Google API Services
Google's API services, such as the Google Maps Platform or the Google Cloud Platform, utilize API keys to authenticate users and restrict access to authorized developers.
Twitter API
The Twitter API uses API keys to allow developers access to its various resources, such as user profiles, tweets, and timelines, while maintaining the security and integrity of the platform.
Stripe API
Stripe, a popular payment processing platform, uses API keys to manage customer data and enable secure payment processing.
Amazon Web Services (AWS)
AWS uses API keys as a part of their authentication system, which facilitates access to various AWS services like Amazon S3, Amazon EC2, and others.
Frequently Asked Questions (FAQs)
What is an API key?
An API key is a unique alphanumeric string used to authenticate and identify users, developers, or applications when accessing a specific Application Programming Interface (API).
Why are API keys necessary?
API keys control access to protect sensitive data and ensure the proper functioning of an API service by granting permissions and restricting access to authorized users.
How are API keys typically stored and passed in requests?
API keys should be stored securely in a dedicated secret management system or an encrypted file. They are usually passed in requests using HTTP headers.
What are some best practices for handling API keys?
Some best practices include: not hardcoding API keys, monitoring usage, implementing regular key rotation, and limiting controls and permissions.
Can you name some popular platforms that use API keys?
Examples include Google API Services, Twitter API, Stripe API, and Amazon Web Services (AWS).