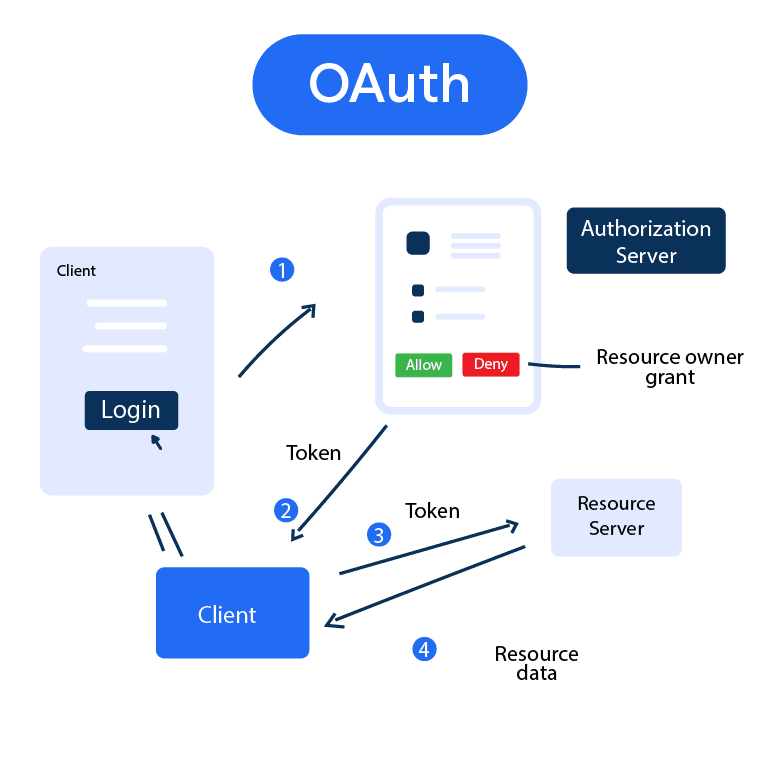
OAuth: An Overview
OAuth is an open-standard authorization protocol or framework that describes how unrelated servers and services can safely allow authenticated access to their assets.
It primarily provides a process for end-users to authorize third-party access to their server resources without sharing their credentials, employing a token-based system.
Who Uses OAuth?
OAuth is widely adopted by tech industry giants and small businesses alike. It is used by web developers, application service providers, and organizations that require secure and streamlined resource access.
Some notable entities that use OAuth include Google, Facebook, and Twitter, which allow users to share their information with other websites or apps without revealing their passwords.
When is OAuth Deployed?
OAuth comes into play when there's a need to access user data or resources hosted on one site by another site, without compromising security.
For example, when users want to log into a third-party website using their Google or Facebook credentials, OAuth is at work.
Also, when applications seek to interact with a user's data stored in a service (like fetching a list of contacts or posting on social media), OAuth is deployed.
Where is OAuth Used?
In the digital realm, OAuth operates wherever there's a need to access user-specific data in a secure manner without the hassle of password management.
This could be across various applications, databases, and platforms on the web. For instance, if a user wants to use a new mobile app and chooses to 'Sign in with Google' instead of creating a new account, the application uses OAuth to authenticate the user.
Why Use OAuth?
OAuth provides a secure and efficient alternative to sharing passwords. By granting tokens instead of credentials, OAuth allows users to authorize third-party applications with diverse levels of access to their data hosted by a specific service.
It supports seamless user experiences, saving users from registrations and remembering multiple passwords, while preserving privacy and security. Plus, for developers, it simplifies the authorization process by providing a standard set of tools and protocols.
Main Concepts and Terminology: OAuth
The main concepts and terminology are:
Access Token
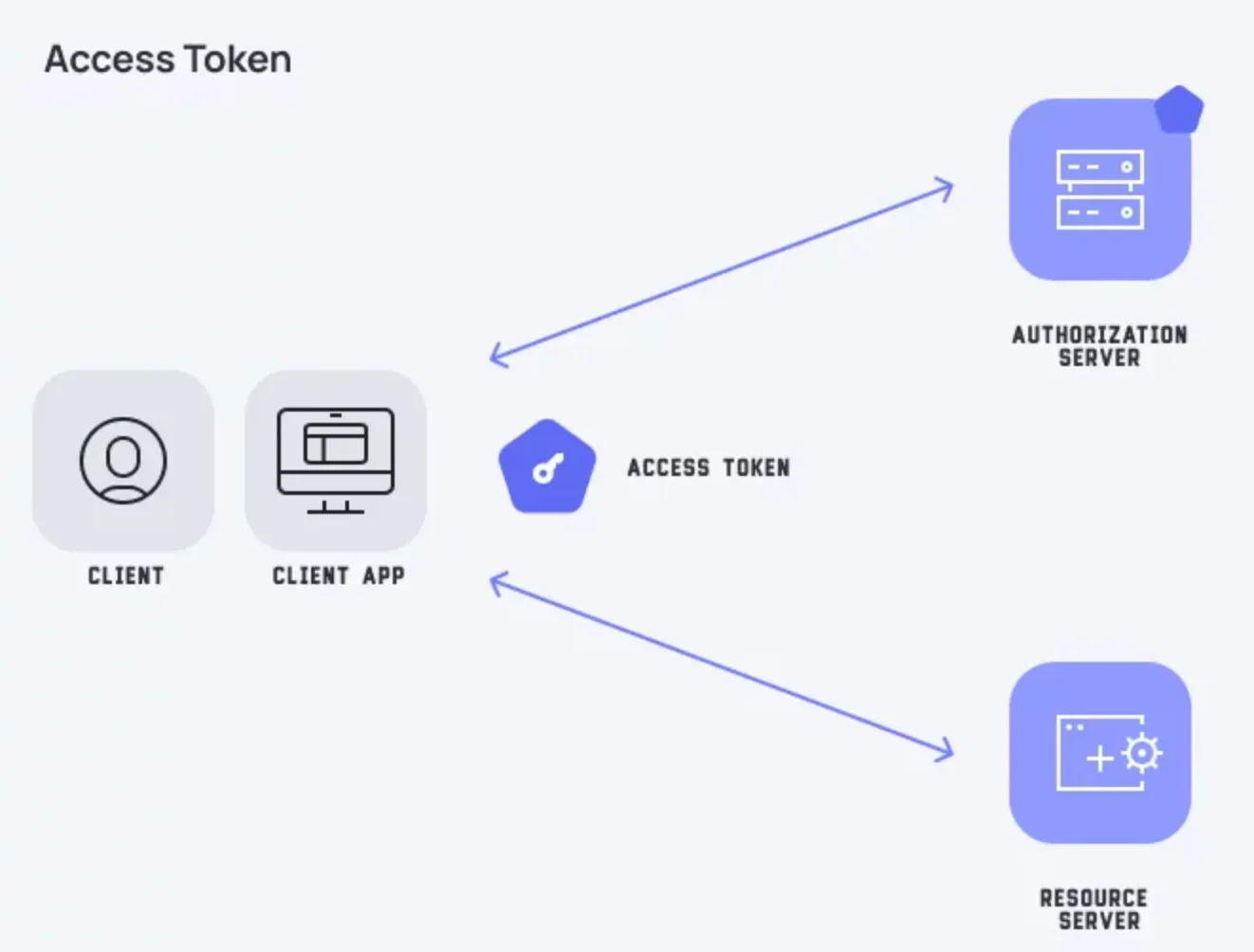
An access token is a credential granted by the authorization server that allows a third-party application to access specific resources on behalf of a user.
It acts as a proof of authorization and is limited in scope and validity.
Authorization Server
The authorization server is responsible for authenticating the user and issuing access tokens to authorized applications.
It plays a crucial role in the OAuth process by verifying the identity of the user and ensuring proper authorization before granting access.
Resource Server
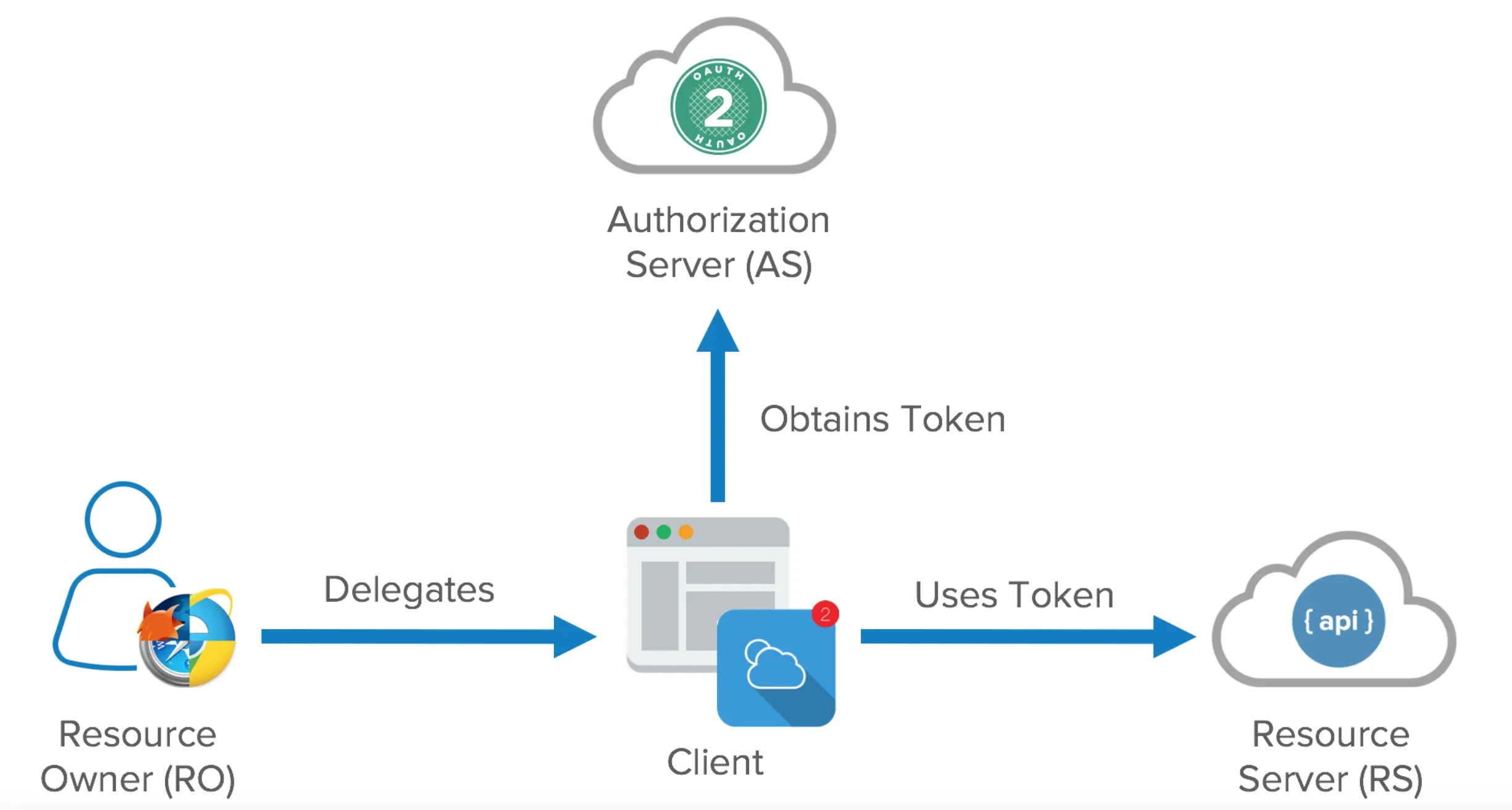
The resource server hosts and manages the protected resources that users want to share with authorized applications.
It protects these resources by validating the access tokens provided by the client applications and enforcing the defined access controls.
Client Application
A client application is an application that requests access to a user's resources.
It interacts with the authorization server and the resource server on behalf of the user, following the OAuth protocol to obtain and use access tokens.
User
The user is the individual who owns the resources and grants access to the client applications.
They interact with the application to authenticate themselves and authorize the access to their data.
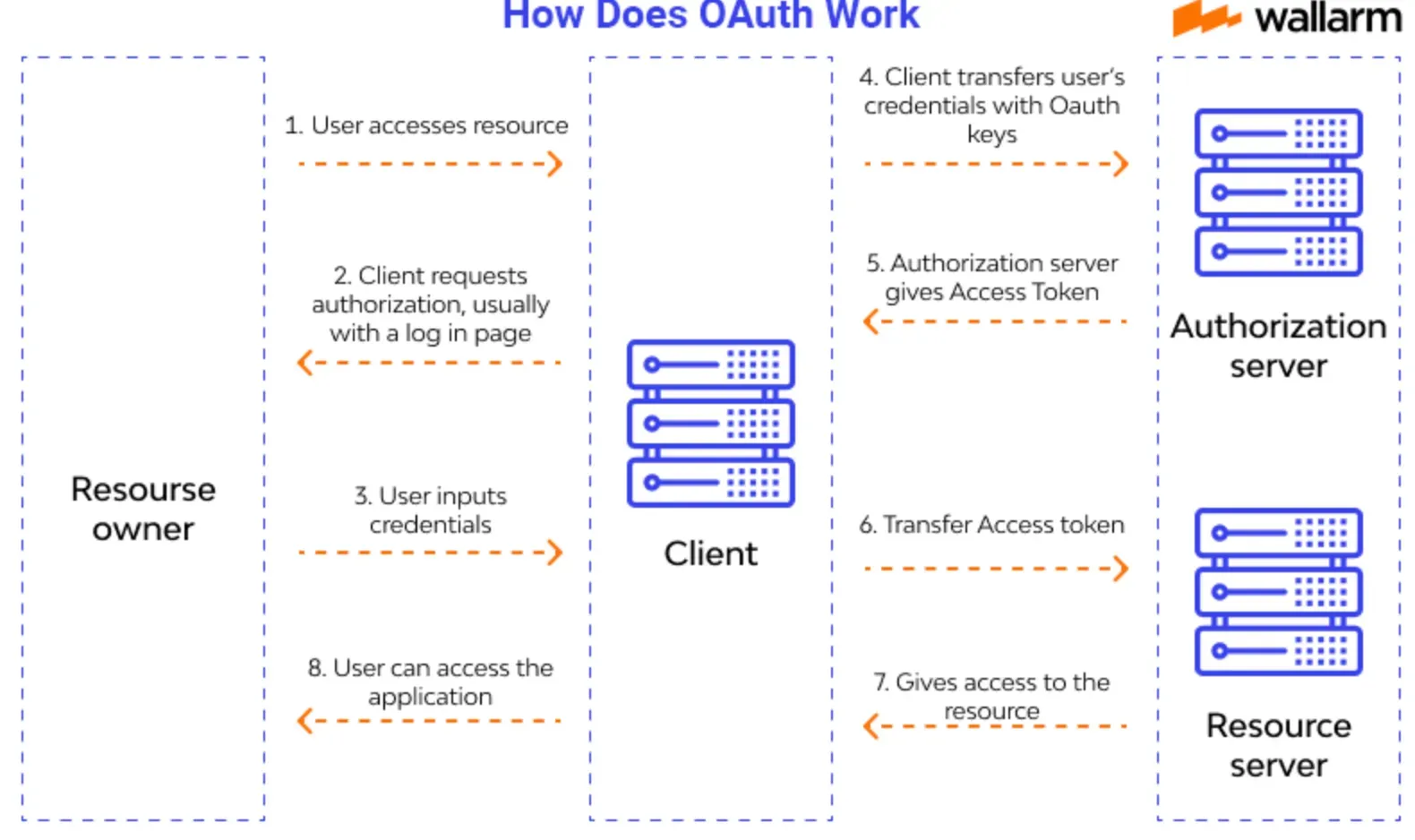
How does Oauth Work?
In this section, we'll break down OAuth, demystifying its process, and taking you through each step that ensures secure access to applications and information.
Requesting Authorization
To kick off the OAuth process, the third-party application (Client) needs to request authorization from the user (Resource Owner).
This typically involves redirecting the user to a login page on the authorization server.
Granting Permission
Once the user successfully logs in, the authorization server presents a consent screen. Here, the user decides which permissions to grant the Client.
Permissions can range from basic profile information to access to specific data or resources.
Issuing the Authorization Code
After the user grants permission, the authorization server generates a unique authorization code.
It then redirects the user back to the Client, providing the authorization code in the process.
Exchanging the Code for an Access Token
Armed with the authorization code, the Client makes a request to the authorization server, exchanging the code for an access token.
The authorization code is a one-time use token only valid for a short period, while the access token is more powerful; it allows the Client to access the user's data from the resource server within the permissions granted.
Accessing User Data
With the access token in hand, the Client can now request the user's data from the resource server. As long as the access token is valid and unexpired, the Client can continue to access the authorized data or resources within the agreed permission boundaries.
OAuth elegantly balances user convenience and security, making it a go-to choice for many applications that require quick access to user data without compromising their credentials.
Benefits of OAuth
OAuth brings numerous benefits to users, application developers, and service providers:
- Enhanced Security: OAuth eliminates the need to share sensitive credentials with third-party applications, reducing the risk of data breaches.
- User Control: Users have granular control over the data they share and can revoke access to specific applications at any time.
- Developer Efficiency: Developers can leverage OAuth to integrate their applications with existing platforms without reinventing authentication mechanisms.
- Seamless User Experience: OAuth enables a seamless and simplified user experience by eliminating the need for repetitive login procedures.
Common Use Cases of OAuth
In this section, we'll explore some of the most prevalent use cases of OAuth (Open Authorization), demonstrating its role in facilitating secure and easy access to online resources.
Social Media Integration
OAuth plays a significant role in enabling integration with social media platforms. Applications can use OAuth to securely access user data stored on these platforms, fostering feature-rich experiences.
For instance, a photo-sharing app might use OAuth to enable users to post pictures directly on their Facebook timeline.
Single Sign-On (SSO)
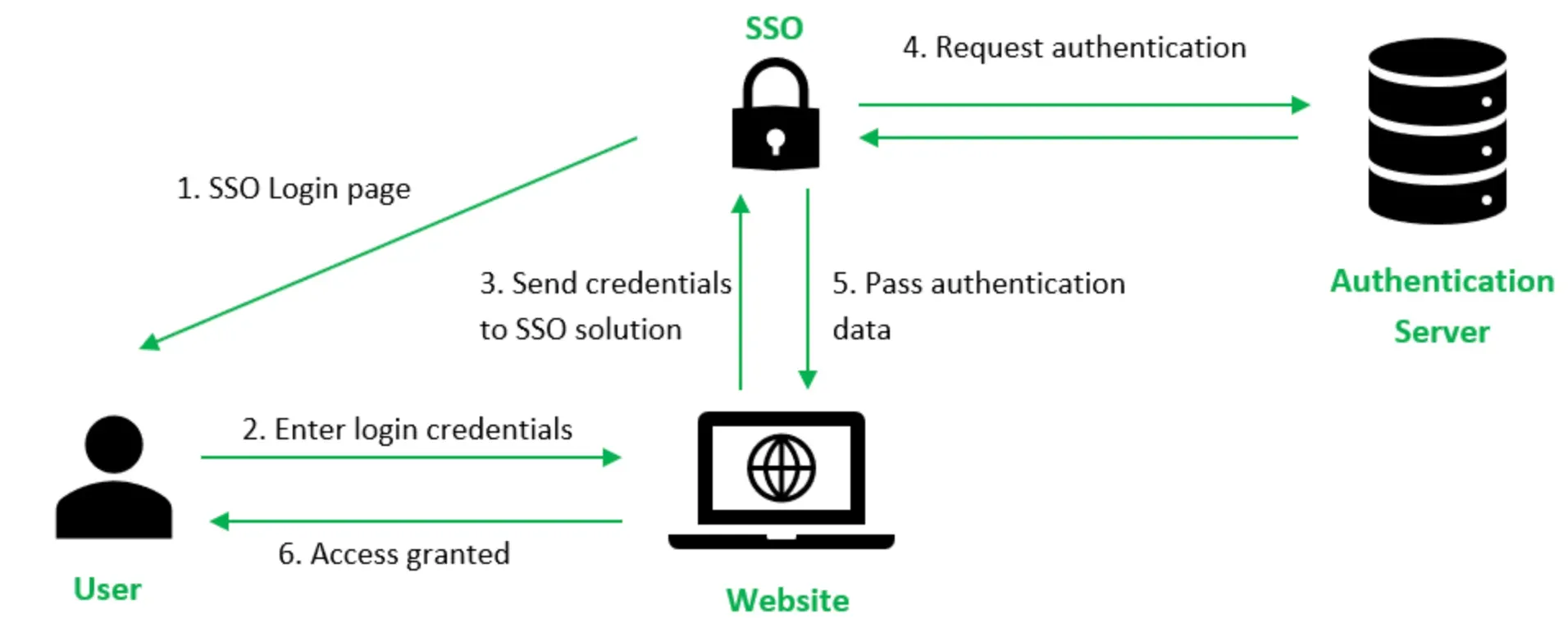
Single Sign-On (SSO) is another common use case that OAuth empowers.
Websites and applications—including platforms like WordPress—can implement WordPress OAuth SSO to allow users to log in using their existing credentials from providers like Google or Facebook, eliminating the need to remember an additional username and password.
Permission-Based Access
OAuth helps implement permission-based access to resources. Users can authorize third-party apps to access specific resources on another service.
For example, a user could grant a printing service access to selected photos in their Google Drive, without compromising other files or folders.
API Access Delegation
With OAuth, you can manage delegated access to APIs. By granting OAuth tokens to software, applications, or services, you can dictate who can perform which operations on behalf of the user.
It's a common practice in modern multi-tier architectures where various microservices communicate with each other.
Third-party Application Authorization
OAuth is often employed to authorize third-party applications, allowing users to interact with another platform's functionality within an app.
An example is a third-party email client that uses OAuth to access emails, send messages, manage folders, and more on a user’s Gmail account.
OAuth vs OAuth 2.0
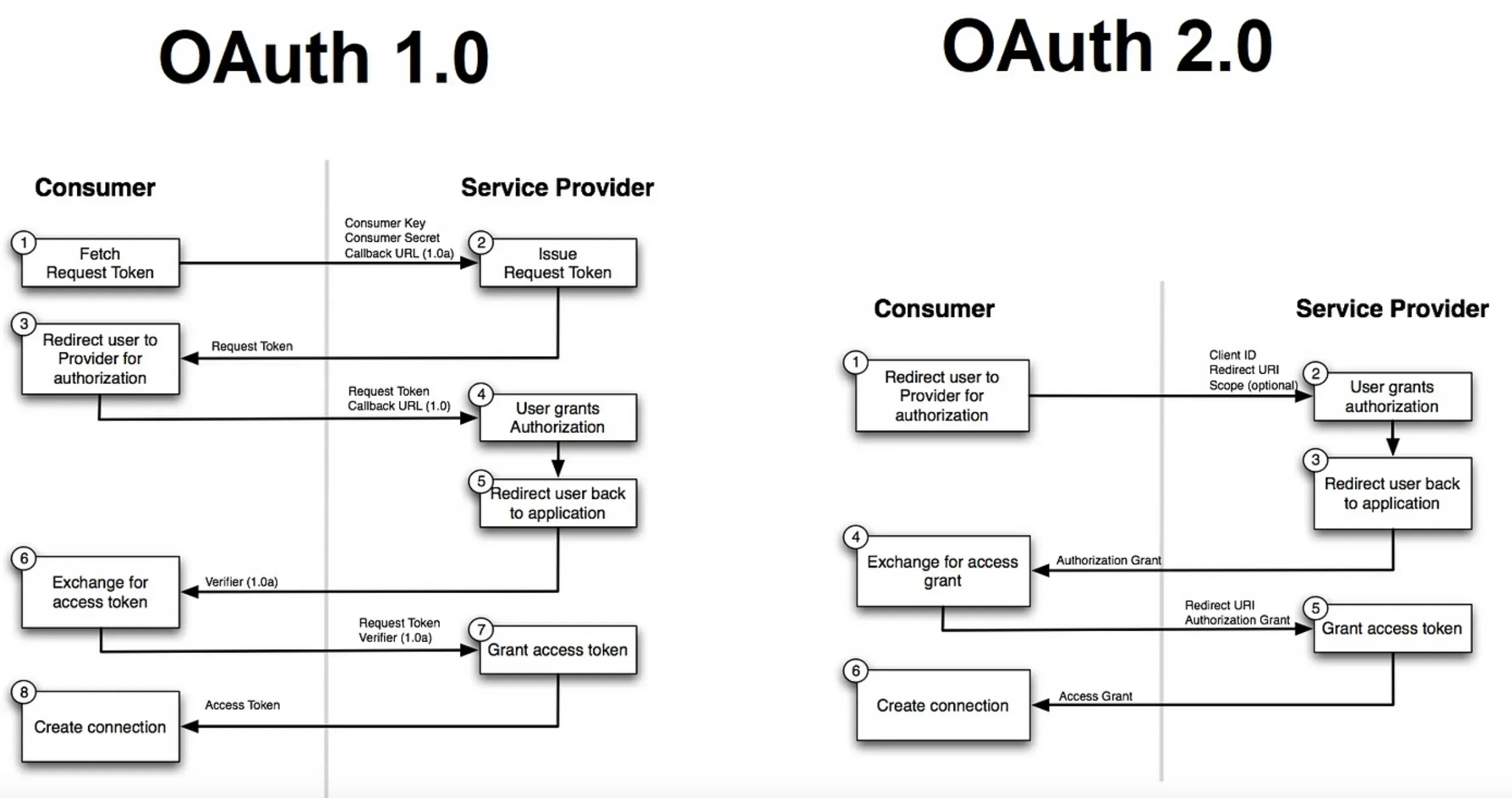
In this section, we'll navigate through the differences between OAuth and its newer version OAuth 2.0, focusing on their primary distinctions and improvements.
Protocol Versus Framework
OAuth was initially introduced as a protocol to facilitate secure API authorization. In contrast, OAuth 2.0 is described as a framework rather than a protocol.
This framework approach in OAuth 2.0 provides greater flexibility and extensibility than the original OAuth.
Security Specifications
While OAuth 1.0 relies on application-level signatures to ensure data integrity and confidentiality, OAuth 2.0 no longer requires such signatures.
Instead, the newest version relies on the use of SSL/TLS for transport-level security, simplifying the process for developers.
Authorization Process
In OAuth, the authorization process involved three-legged OAuth, requiring interchange of numerous tokens between server and client. This process was complex and cumbersome.
OAuth 2.0 simplifies this by introducing two-legged OAuth, streamlining the authentication exchanges between service providers and consumers.
Flexibility and Extensibility
OAuth 2.0 offers more flexibility and extensibility than its predecessor. It wraps different "grant types" into one, such as authorization code, password credentials, client credentials, and others.
This makes it adaptable to various scenarios and situations which could not be easily tackled by plain OAuth.
User-Friendly
OAuth 2.0 is designed to be more user-friendly for developers. It is less prescriptive than the original OAuth and leaves certain decisions up to the implementer.
While this has led to some criticism about consistency and interoperability, it nonetheless makes this newer version easier to use and implement.
OAuth Security Considerations
In this section, we'll dive into the security considerations surrounding OAuth, highlighting the precautions to ensure the robustness of this authorization protocol.
Understanding the Security Model
At the heart of OAuth is its security model, which is designed to safeguard user data while facilitating seamless access to third-party applications.
It achieves this through tokens, acting as intermediaries, thus eliminating the need for third-party apps to store sensitive user credentials.
Watch Out for Leaky Redirects
A minor slip, like a misconfigured redirect URI on the client or authorization server, can be a major security loophole.
Hackers could exploit this to gain unauthorized access tokens, making it crucial to validate and only whitelist trustable redirect URIs.
Safeguard the Access Tokens
Access tokens are like keys to a user's data kingdom. If stolen, they can cause significant damage.
Implementing mechanisms like HTTPS to protect against token interception and limiting the token's scope and lifespan can provide additional layers of security.
Phishing Attacks and Code Interception
OAuth isn’t immune to phishing attacks. An attacker could trick users into granting permissions to a malicious client.
Moreover, the one-time authorization code could be intercepted during the redirection phase. To prevent this, employ PKCE (Proof Key for Code Exchange) technique for public clients.
Get User Consent Right
Often overlooked, but critical in OAuth is the user consent screen. It should clearly communicate the permissions being requested, giving users control over their data.
This transparency not only boosts user trust but also meets legal data privacy requirements.
While OAuth has significantly streamlined authorization, it's imperative to stay on top of these security challenges. Remember, a well-implemented OAuth is a secure OAuth!
Frequently Asked Questions (FAQs)
What is OAuth used for?
OAuth is used for granting third-party applications secure and controlled access to a user's resources, without sharing credentials.
What is an example of OAuth?
Facebook, Google, and Twitter are examples of websites that use OAuth. When a user logs in to another site using their Facebook account, they are authenticating themselves and granting access to their resources.
Is OAuth secure?
Yes, OAuth is secure and provides a standardized method for authorizing access to resources. It eliminates the need for users to share their login credentials with third-party applications.
What is an access token in OAuth?
An access token is a credential that allows a third-party application to access specific resources on behalf of a user. It is limited in scope and validity and acts as proof of authorization.
What is an authorization server in OAuth?
The authorization server is responsible for authenticating the user and issuing access tokens to authorized applications. It plays a crucial role in the OAuth workflow and ensures proper authorization before granting access.
How can I implement OAuth on my website or application?
You can implement OAuth by following the defined protocol and utilizing pre-built libraries or software development kits. It is important to properly plan and design your implementation to minimize any potential risks or limitations.