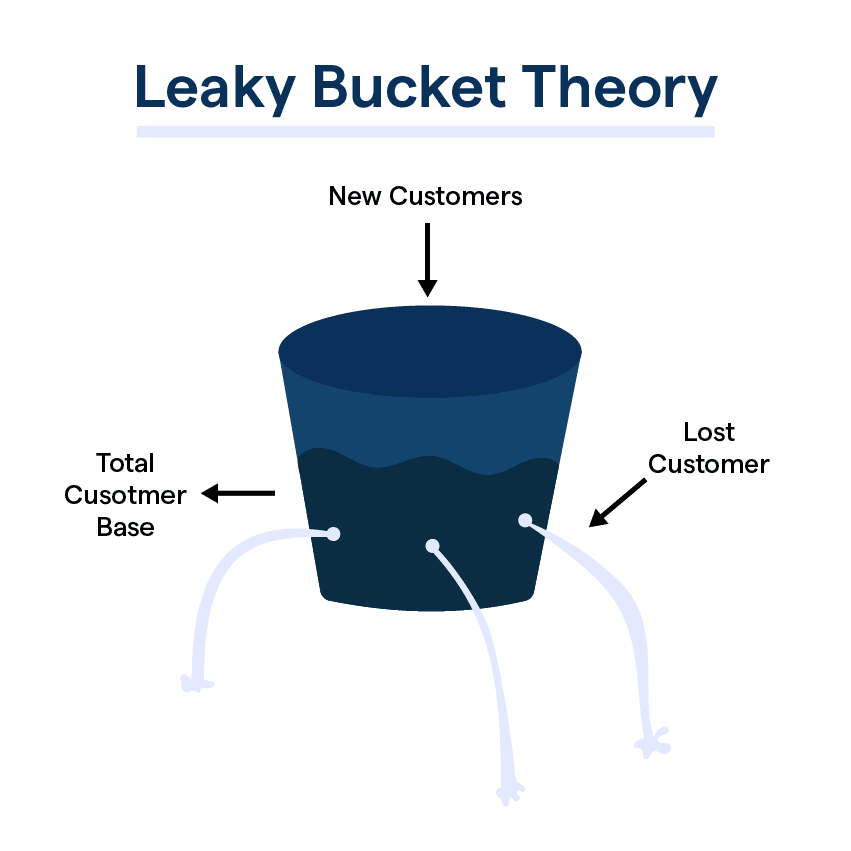
What is Leaky Bucket Theory?
Leaky Bucket Theory, often used in telecommunications and computing, is a metaphorical model used to understand the behavior of different types of data transmission. It implements a constant transmission rate regardless of bursty or irregular traffic.
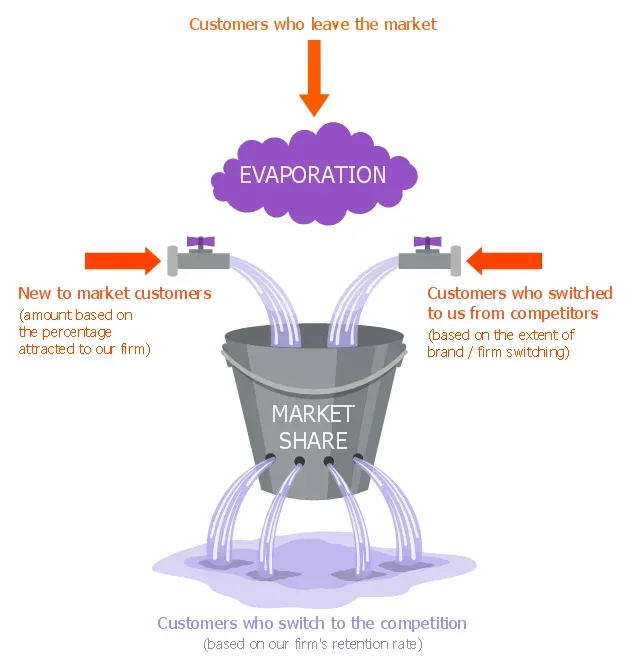
The theory helps in smoothing out bursts of traffic, which is crucial in fields like computer networks and telecommunication. It is designed to provide consistent behavior when dealing with high surges, thereby preventing network congestion.
Key Components
The Leaky Bucket Theory has three critical components: The bucket, the tap, and the leak. The bucket holds the data, the tap represents the incoming data, and the leak is the outgoing data regulated at a constant rate.
Working of the Leaky Bucket
Upon arrival, data packets are sent to the bucket. If the incoming rate exceeds the bucket's capacity, data packets overflow and are considered lost. The leak, at a steady rate, clears packets from the bucket.
Leaky Bucket Algorithm
The Leaky Bucket Algorithm is a congestion control method applied in packet-switched computer networks and telecommunications networks. It provides an efficient way to control the rate of traffic and manage bursty network data transmission.
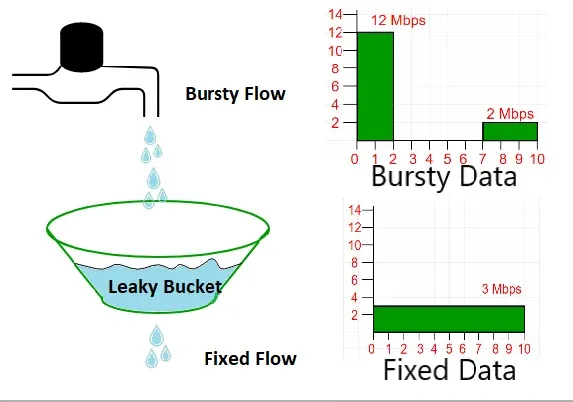
Implementation of the Algorithm
The algorithm uses the Leaky Bucket Theory to control data congestion in networks. As packets arrive, they are sent to the 'bucket.' If the incoming rate is too fast and the bucket overflows, excess packets are discarded.
Advantages of Leaky Bucket Algorithm
The algorithm ensures a constant output rate, making network traffic predictable and manageable. It also keeps the network from being flooded by a sudden burst of data packets.
Disadvantages of Leaky Bucket Algorithm
In case of an idle incoming line, a leaky bucket may continuously leak at a constant rate, which could be a major disadvantage. Plus, any overflow in the bucket leads to packet loss.
Real-world Applications of Leaky Bucket Theory
Leaky Bucket Theory, along with its algorithms, are widely used to handle congestion control in computer networks. They help smooth out sudden high data traffic bursts and enable consistent data transmission.
In Video Transmission
The Leaky Bucket theory is pretrained in video transmission, an area often marked by inconsistent and bursty data flow. It helps standardize and regulate the frame rate for smooth video transmission.
In Traffic Shaping
It also plays a critical role in traffic shaping or packet shaping, which involves controlling the volume of data that's sent out over a network at a particular speed, thus preventing traffic congestion.
As a Metaphor
The Leaky Bucket theory is also utilized as a metaphor in customer churn rate scenarios, highlighting customer loss (leak) against acquisition (input).
Comparison with Token Bucket Algorithm
The Token Bucket is another algorithm commonly used in packet-switched networks. It allows for network bursts and doesn't discard packets once the bucket fills to capacity, instead storing them to process later if possible.
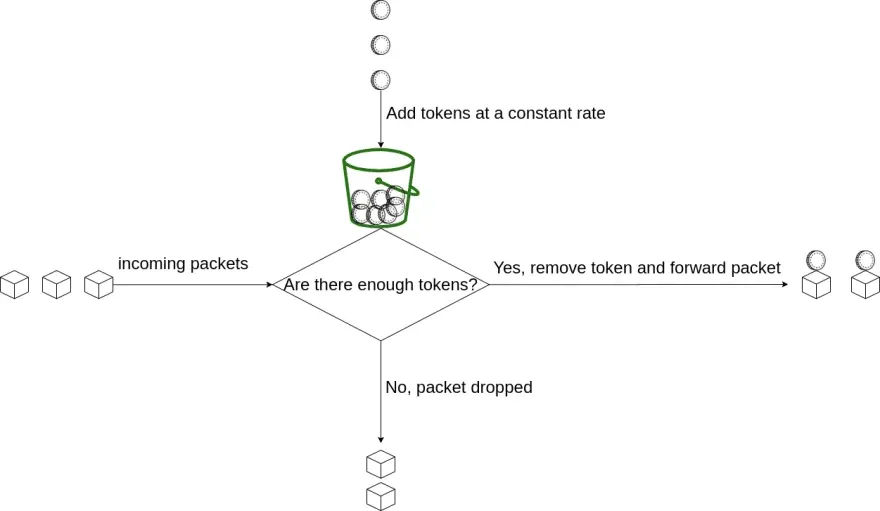
Implementation of Token Bucket Algorithm
In this algorithm, 'tokens' are added at a certain rate to a bucket. When a packet needs to be managed, it uses these tokens. If enough tokens exist, the packet is sent. If not, the packet awaits until tokens are generated.
Differences from Leaky Bucket
Unlike Leaky Bucket, the Token Bucket allows for bursty traffic since it doesn't strictly limit output rate. It's more flexible as it uses tokens to decide when data packets can be sent.
Similarities with Leaky Bucket
Both algorithms aim to moderate bursty traffic and prevent network congestion. They use a similar bucket metaphor where incoming data fills the bucket and the outgoing data is regulated.
Limitations of Leaky Bucket Theory
One of the challenges is that it discards excess packets when the bucket overflows - a condition caused due to high bursts of traffic.
Idle Bucket
In the absence of incoming data, a leaky bucket continues to leak at a constant rate. This behavior leads to inefficiency in data transmission.
Complexity
Implementing the Leaky Bucket algorithm could add complexity to data transmission processes.
No Burst Handling
The Leaky Bucket algorithm can't handle sudden traffic bursts as it has no provisions for storing or buffering overflow data for future use.
Frequently Asked Questions (FAQs)
What is the Leaky Bucket Theory and where is it used?
Leaky Bucket Theory is a metaphorical representation of how data is transferred at a fixed rate regardless of data traffic. It's commonly used in telecommunications and computing.
How does the Leaky Bucket Algorithm work?
The algorithm handles incoming data packets and dispatches them at a constant rate. If the incoming rate exceeds the 'bucket' capacity, the excess packets are discarded.
What is the difference between the Leaky Bucket and Token Bucket Algorithms?
While both aim to prevent network congestion, they differ in their approaches. Leaky Bucket discards excess packets and maintains a constant output rate, whereas Token Bucket allows for bursty traffic and doesn't limit the output rate strictly.
What are the limitations of the Leaky Bucket Theory?
Possible limitations include packet discarding in case of overflow, inefficiency during idle times, complexities in implementing the associated algorithm, and inability to handle sudden traffic bursts.
How does the Leaky Bucket Theory helps in real-world applications?
It plays a key role in computer networks for congestion control. It also aids in video transmission, traffic shaping, and metaphorically helps understand scenarios like customer churn rate.