What is Two-Factor Authentication?
Two-factor authentication, or 2FA, as it's commonly known, is all about protection from cyber-attacks by providing two layers of passwords.
Imagine it as a two-tier security measure where you need to cross two different kinds of checkpoints to confirm that it's indeed you.
Broad categories of these checkpoints include three fundamentals - something you know (like a secret password or a PIN), something you own (like your smartphone or security token), and something you are (like your biometric details such as facial recognition or fingerprints).
The significance of 2FA lies in its simple yet effectual concept - it makes breaking into your account much harder.
Even if your primary password falls into the wrong hands, they'll still need another checkpoint clearance to gain entry.
You might not even realize it but with each ATM transaction, where you use your debit card (something you possess), and then put in your unique PIN (something you know), you're basically employing 2FA.
The Importance of Adopting Two-Factor Authentication
Now that we understand what 2FA is, it's vital to comprehend why it's a must-have in today's increasingly digital age.
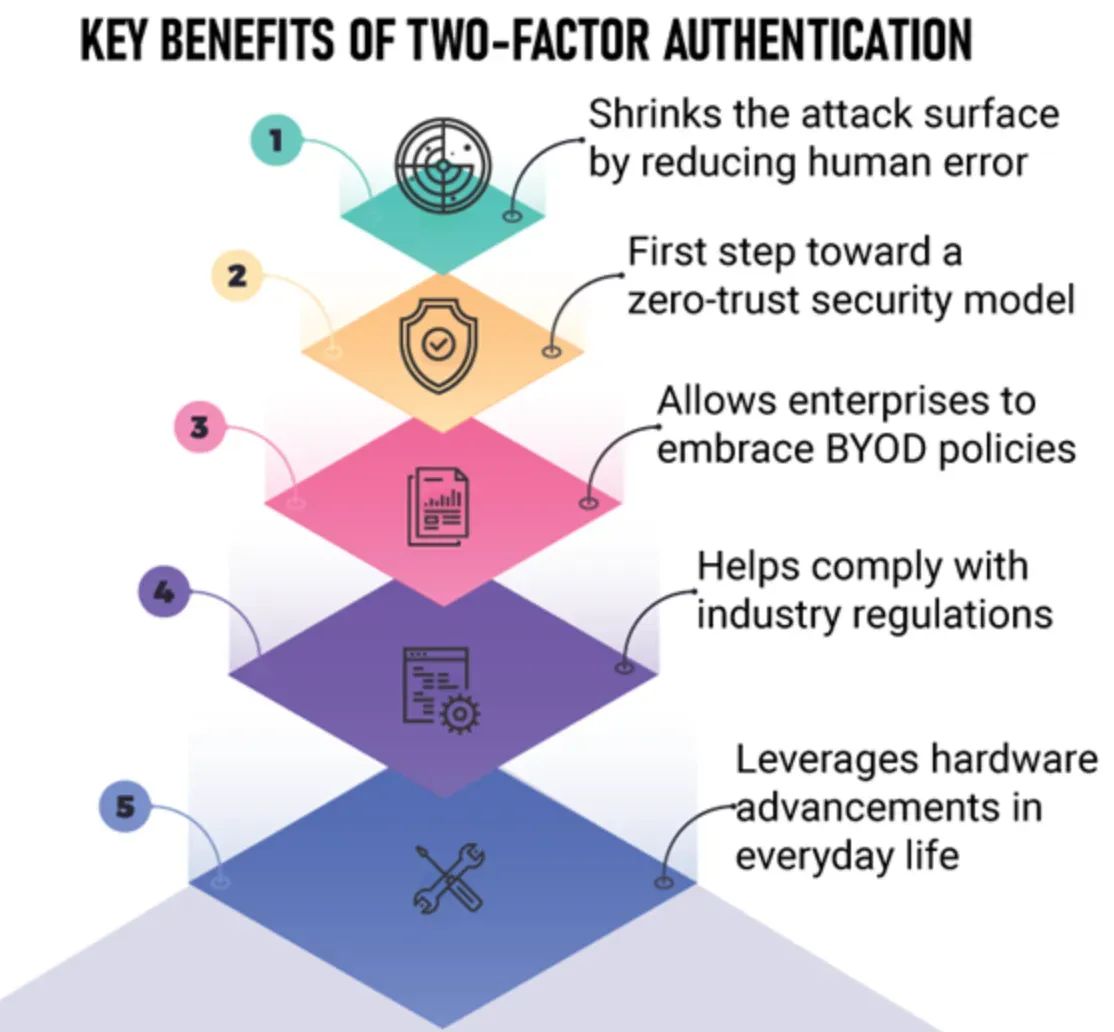
Enhanced Security
There can't be enough emphasis placed on the fact that 2FA takes your account security a notch up. Your password alone is no longer the lone guardian of your data.
Cutting Down Identity Thefts
The rate of online scams and identity thefts has skyrocketed. With 2FA, you're keeping this risk at bay. Even if an unauthorized person gains access to your password, they still can't log into your account without crossing the second checkpoint.
Pushing Back Against Phishing Attacks
2FA is your first defense line against phishing. Your password may get into wrong hands through a deceptive link or tool but the next barrier of 2FA will bar their entry into your accounts.
Building Trust through Assurance
In business, trust is as crucial as the services or products you offer. Implementing 2FA clearly communicates to your users and clients that their data is of paramount importance and you're employing tough measures to protect it.
Optimal Usage of Two-Factor Authentication
Wherever there's a need for an additional security layer, there's room for 2FA. Here are some instances.
Safekeeping Online Banking Transactions
Banks usually prefer the SMS-based verification method for every transaction to keep your money safe.
Shielding Personal Social Media Accounts
With all the personal data you put on these platforms, 2FA is the safety net you need.
Bolstering Security for Emails and Cloud-based Services
Email accounts typically contain sensitive information. With the incorporation of 2FA, unlawful access can be prevented.
Securing Healthcare Records
Patient health information or PHI is sensitive data that needs to be protected fiercely. Including 2FA could make these systems more secure.
Implementation of Two-Factor Authentication across Industries
While not limited to particular sectors, certain businesses can gain immensely from 2FA adoption.
Websites
Websites asking for user login details can create a 2FA procedure to assure users that their data remains secure.
Software Applications
Applications, especially ones dealing with sensitive user data like banking or health apps, can use 2FA for an extra layer of security.
Physical Equipment
Certain devices like some hi-tech locks need both a physical key and a unique code to unlock, effectively using 2FA.
Personal Electronic Devices
Personal gadgets such as tablets, laptops, or mobile phones can be safeguarded through 2FA procedures.
Best Practices for Two-Factor Authentication (2FA)
Two-factor authentication significantly improves the security of online accounts. Here are some best practices to ensure its effectiveness.
Use Authenticator Apps Instead of SMS
While SMS is an available option for 2FA, it has weaknesses due to its susceptibility to hacking techniques like SIM swapping or interception. Using an authenticator app such as Google Authenticator, Authy, or Microsoft Authenticator is considered safer.
Regularly Review Your Security Preferences
Security isn't a set-and-forget thing. Conduct regular reviews of your security settings and preferences. Be aware of any new cybersecurity threats and adjust your settings accordingly.
Encourage User Education
If you're implementing 2FA for a business, regularly educate your employees about the importance of 2FA. An informed userbase can protect the company from potential security attacks.
Have a Backup Plan
Always have a backup option in case your primary device for 2FA gets lost or stolen. Some services provide backup codes that you can keep offline or print.
Avoid 2FA via Email
Email-based 2FA is less secure than authenticator apps or physical security keys due to the potential for email to be intercepted. Avoid if possible, and use more secure options.
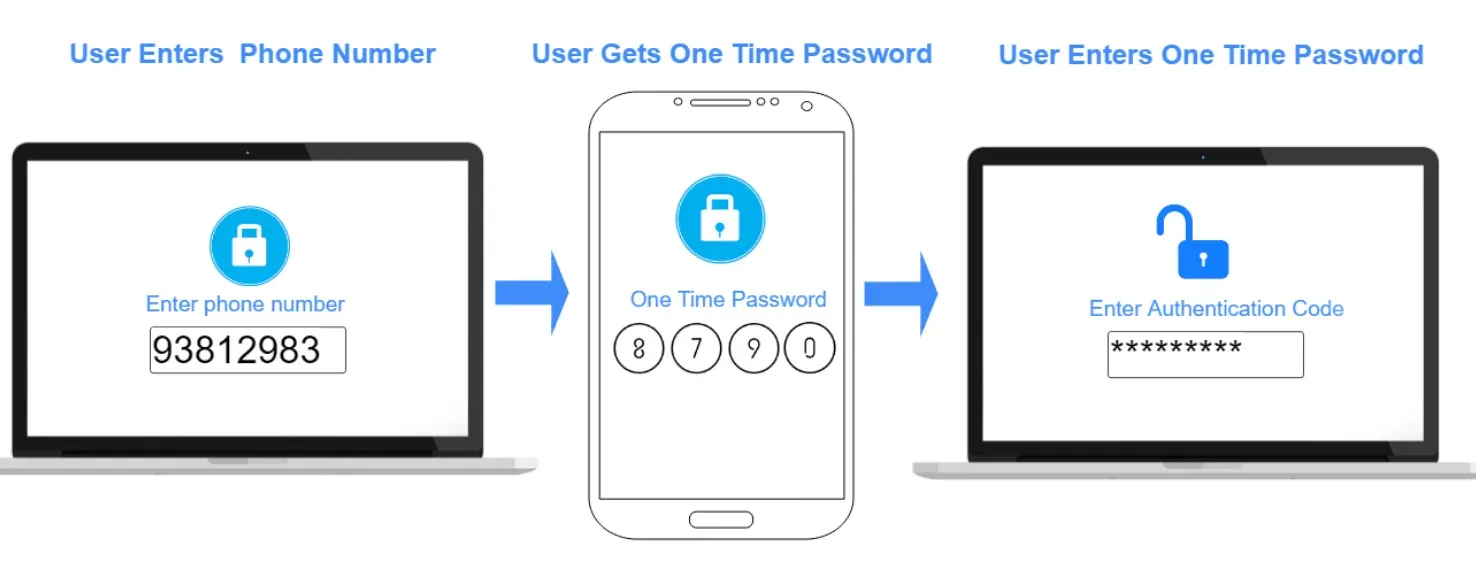
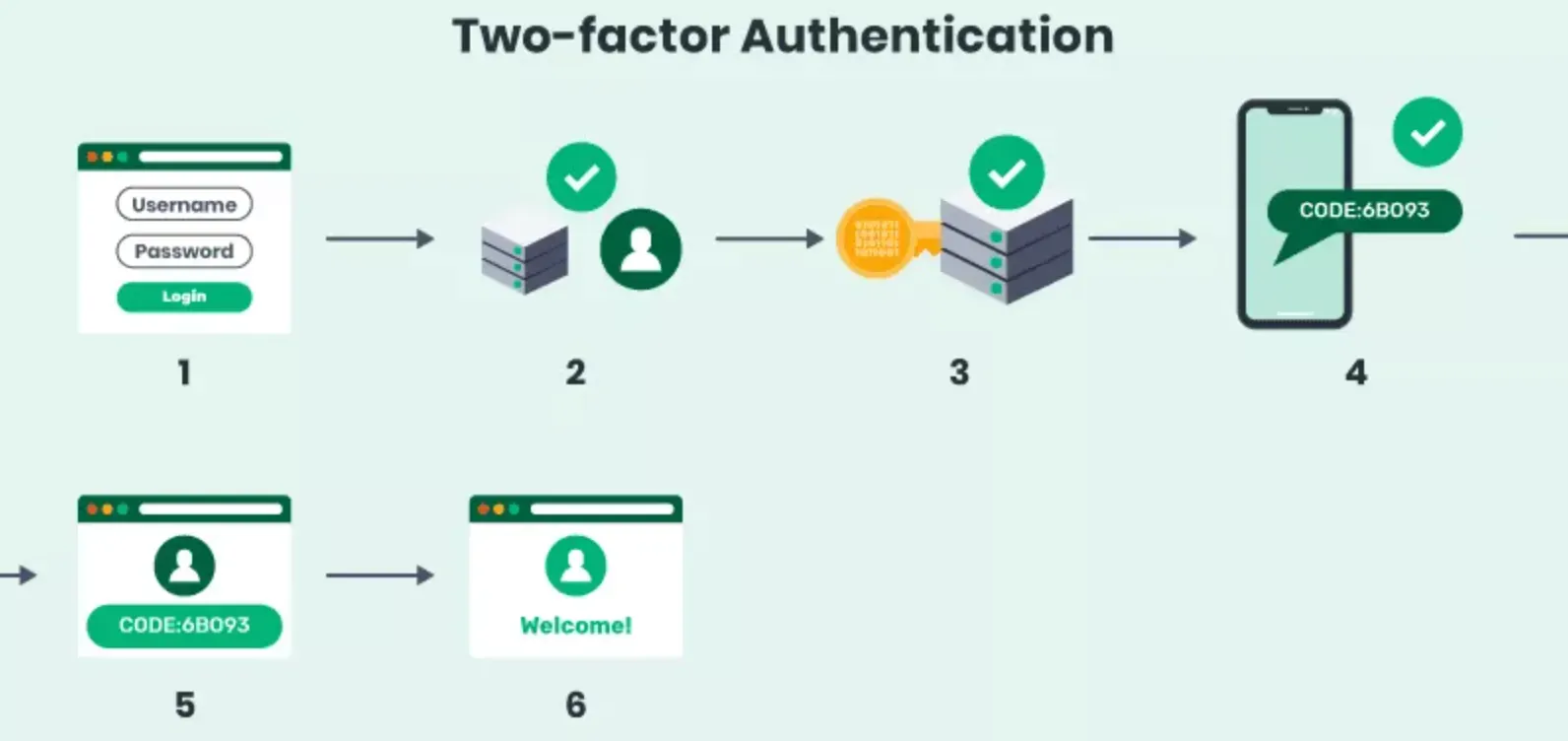
Step By Step Guide for Two-Factor Authentication
Implementing 2FA for your online accounts is a straightforward process but may vary slightly depending on the specific platform. Let's discuss a general step-by-step approach for 2FA.
Step 1
Decide the 2FA Method
Decide between SMS, email, authenticator apps, or physical security keys for your second factor. Remember, authenticator apps or physical keys are the most secure options.
Step 2
Set Up on the Platform
Navigate to the security settings of your account. Most platforms have a section for "Two-Factor Authentication" or "2FA". Follow the steps outlined to enable it.
Step 3
Sync Your Device
For authenticator apps, scan the QR code provided or manually enter your key. This will sync your device and the platform. For SMS or email, enter the necessary contact information.
Step 4
Verify the Setup
Once you've synced your device, a code will be generated or sent to you. Enter this on the platform to verify the setup.
Step 5
Save Backup Codes
Once you've set up 2FA, make sure to save backup codes in a safe, offline place. These can prove helpful if you lose your primary device.
Remember, your approach may vary slightly depending on the platform and 2FA method chosen, but these steps provide a good starting guide.
Addressing Challenges Associated with Two-Factor Authentication
Including 2FA comes with its own set of challenges.
Issues with User Convenience
For some users having an extra step for logging in might be cause for inconvenience and might even act as a deterrent from using your products.
Dependence on Electronic Devices
In situations where a user might lose their security device, alternative procedures must be in place.
Facing Sophisticated Cyberattacks
2FA doesn't provide an invincible shield, there are cases where sophisticated attacks have circumvented 2FA. It points towards the need for continuous vigilance and updates.
Potential Implementation Costs
For companies, the cost of setting up, maintaining, and updating 2FA procedures could be a deterrent. Still, it must be remembered that investing in data security is a critical facet of modern businesses.
Frequently Asked Questions (FAQs)
Is 2FA an Invincible Shield against Cyberattacks?
Even though 2FA significantly improves security, it's not a foolproof barrier. Advanced threats can oftentimes bypass it considering this it's imperative to maintain proactive security measures.
If I'm Not Dealing with Critical Data, Is 2FA Necessary?
Even if you believe your data isn't important, it's better to be safe than sorry. Adopting 2FA makes your online accounts far less attractive to potential cyber invaders.
How Secure is SMS-Based 2FA?
Though more secure than having no 2FA, SMS-based 2FA has its risks including SIM swapping or interceptions. Authenticate apps or physical security tokens present more secure alternatives.
Can you Use Third-Party 2FA Tools?
You can use various third-party 2FA solutions like Google Authenticator, but always remember to verify their credibility and privacy measures.
Does 2FA have an Impact on User Experience?
2FA might initially seem like a nuisance, but users must realize that this extra step essentially is there for their security. Informing users about its benefits could make them more accepting of it.