What is Intrusion Detection?
Intrusion Detection is a cybersecurity process that monitors network or system activities for malicious activities or policy violations. It uses software and hardware to identify unauthorized access attempts or attacks. Intrusion Detection Systems (IDS) alert administrators of potential threats, helping to safeguard information systems from breaches and ensuring data integrity and security.
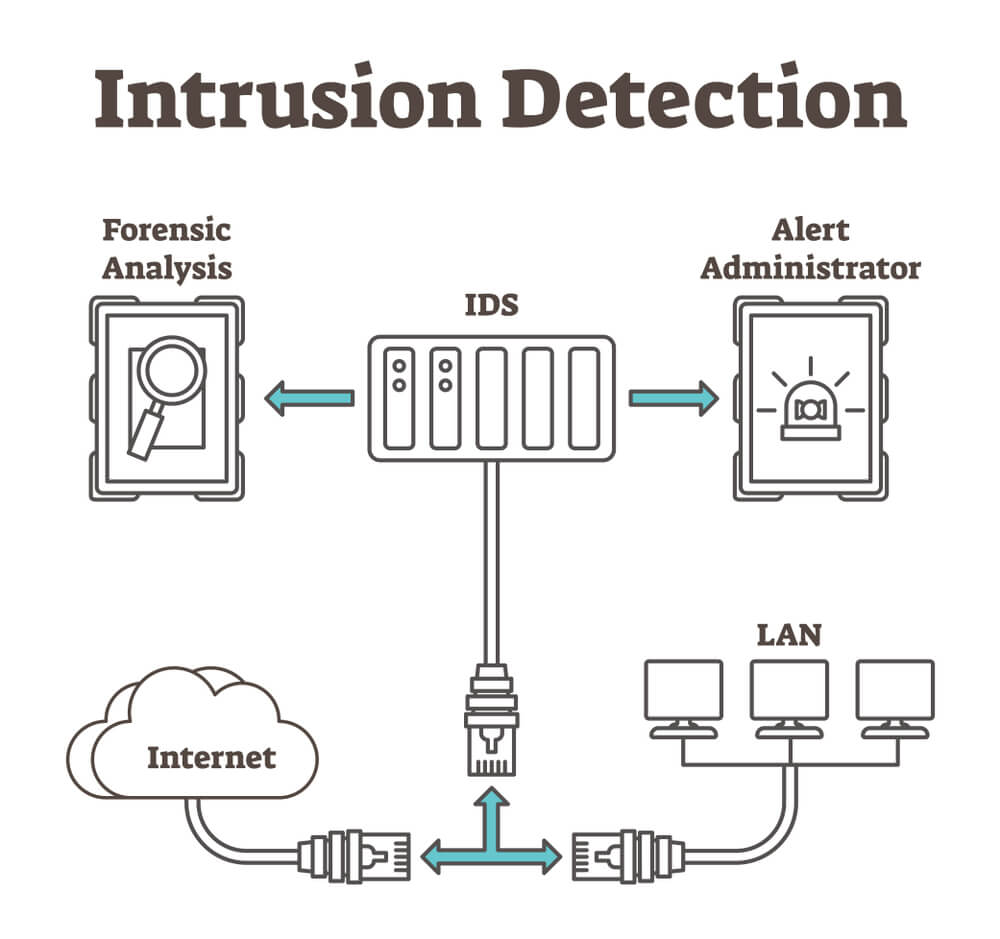
Importance of Intrusion Detection Systems (IDS)
These systems are the unsung heroes. They work behind the scenes to keep the digital bad guys out. Imagine locking your doors at night, but for your computer network. That’s what an IDS does - it makes sure no one gets in without permission.
Types of Intrusion Detection Systems (IDS)
Different types of intrusion detection system are the following:

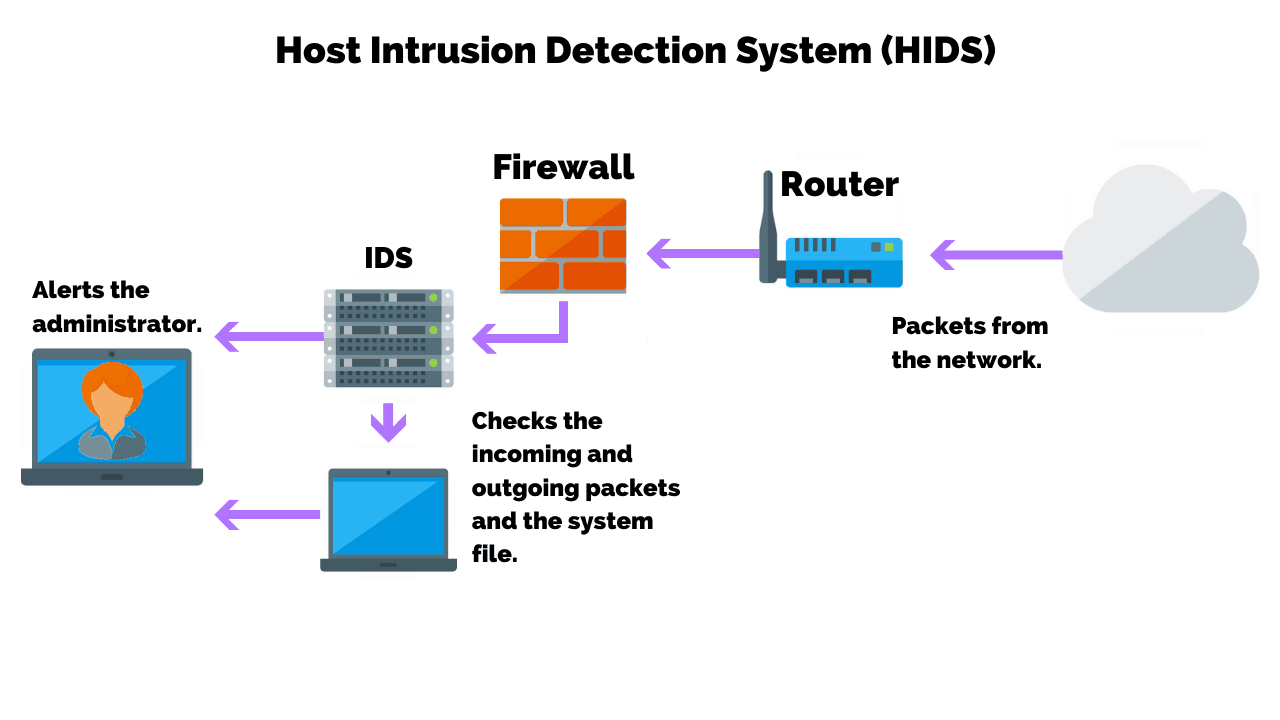
Host-based IDS (HIDS)
This one’s like a personal bodyguard for your computer. It watches over everything happening inside the machine, ready to sound the alarm if anything fishy pops up.
Network-based IDS (NIDS)
Imagine a guard scanning everyone who enters a building. That’s NIDS, but for your network. It keeps an eye on the data moving in and out, looking for anything out of the ordinary.

Hybrid IDS (HIDS)
Why choose when you can have both? Hybrid IDS combines the best of both worlds, offering tight security inside your devices and on your network. It’s like having surveillance cameras inside and outside your house.
In crafting security strategies, some might say chatbot developers can play an unexpected role.
How Intrusion Detection Works
In this section, you’ll find how intrusion detection works:
- Signature-based Detection :Think of it like a list of no-nos. Signature-based detection has a bunch of red flags it looks out for. If it sees any, it rings the alarm!
- Anomaly-based Detection :This method is all about sensing the weird stuff. If your computer's behavior starts to look different from the usual, anomaly-based detection gets suspicious and takes note.
- Behavior-based Detection: Behavior-based detection is like an old friend who knows you super well. The moment you start acting off, it notices. Replace "you" with your computer system, and that's how it works.
Components of an Intrusion Detection System
Different components of intrusion detection system are the following:
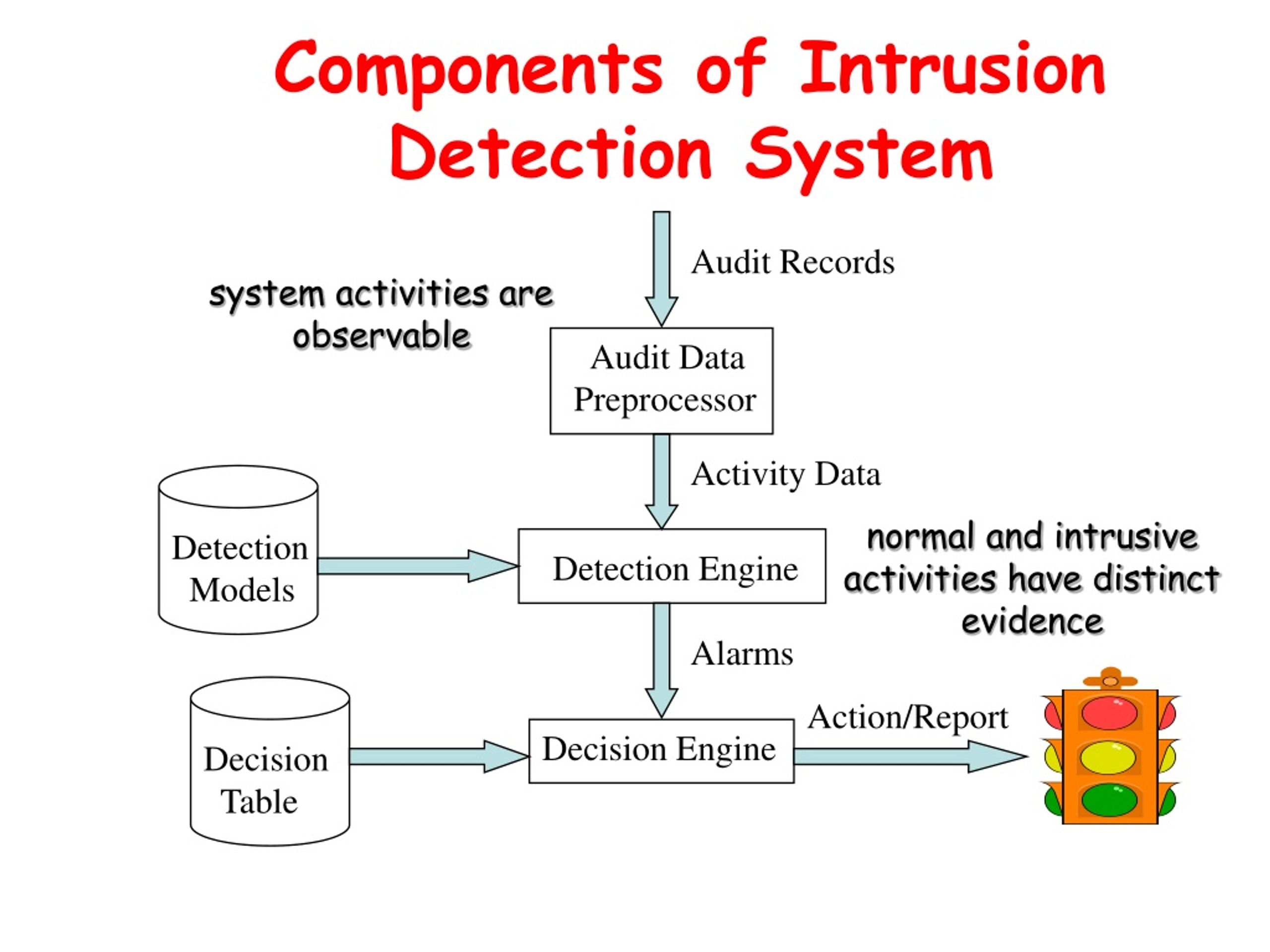
- Sensors :Sensors are the ears on the ground. They listen to all the data and pick up on anything odd, sending the details to the brain of the operation.
- Analyzers :The analyzer is the brain itself. It takes all the info from the sensors and thinks it over, deciding if it's a real threat or just a false alarm.
- User Interface :And the user interface, that's your window to the system. It lets you see what's happening and control the settings—simple and straightforward.
Benefits of Intrusion Detection Systems
The benefits of intrusion detection systems are the following:

- Early Detection: IDS helps in the early detection of potential security breaches by identifying suspicious activity that deviates from the established norm.
- Visibility: It provides visibility into the network's traffic patterns and can highlight areas of concern that might require additional security measures.
- Real-Time Alerts: IDS offers real-time alerts when potential security incidents occur, allowing for swift action to mitigate risks.
- Compliance: Many regulations and industry standards require the use of intrusion detection systems, so having an IDS in place can help an organization maintain compliance with legal and industry requirements.
Challenges in Intrusion Detection
The challenges of intrusion detection systems are the following:

- False Positives :False positives are like fire alarms that go off when you're just making toast. They're annoying and can make you ignore real threats.
- False Negatives: Even worse are false negatives—think of a guard dog snoozing when a burglar is sneaking in. It's when bad stuff slips through unnoticed.
- Scalability Issues: When your system grows, sometimes the IDS can't keep up. It's like a net full of holes getting bigger—more things can slip through.
Intrusion Detection vs. Intrusion Prevention
Intrusion detection tells you when trouble is afoot. Intrusion prevention stops trouble in its tracks, like a bodyguard blocking the door.
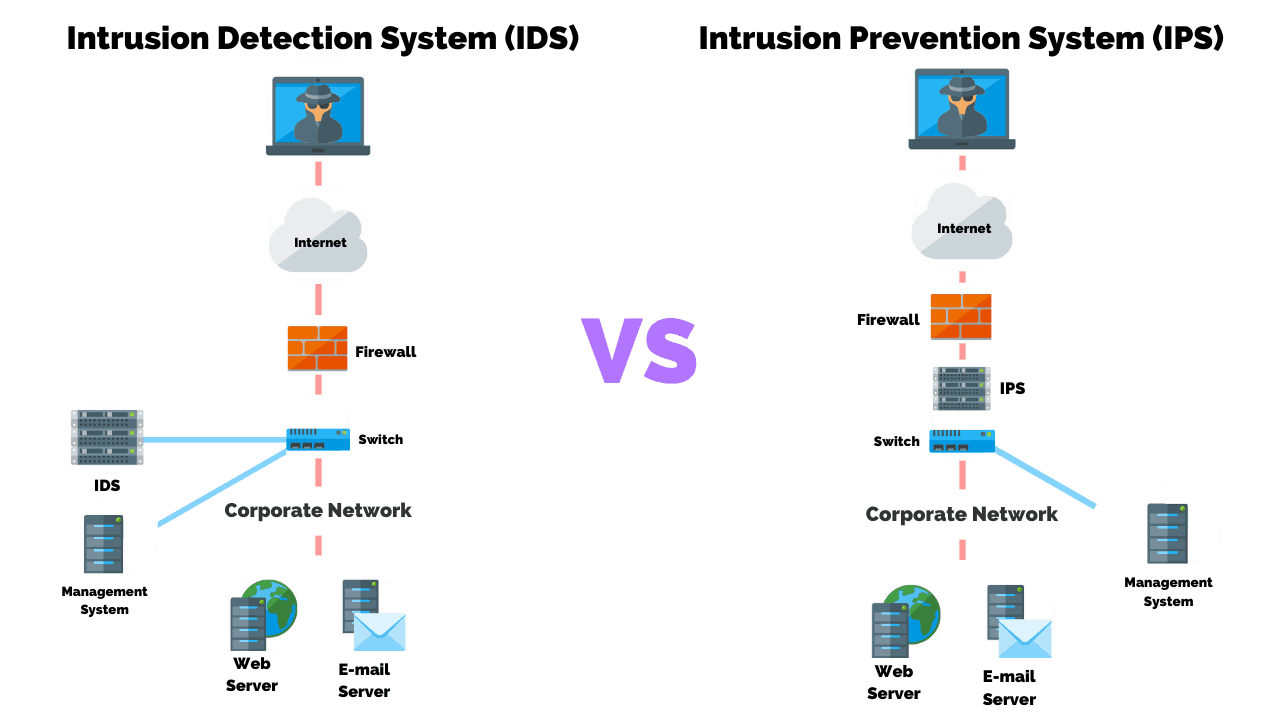
- Complementary Roles in Cybersecurity: They team up for tight security. One watches your back, and the other acts like a bouncer, keeping the dodgy characters out.
- Intrusion Detection Techniques: Different types of intrusion detection techniques are the following:
- Signature-based Techniques :Signature-based techniques match patterns to known villains, like recognizing the face of a wanted poster.
- Anomaly-based Techniques: Anomaly-based techniques are all about spotting strange behavior—like someone dancing in the rain with no music.
- Machine Learning in Intrusion Detection :Machine learning in intrusion detection gets smarter over time, like a detective piecing together the puzzle after seeing enough crime scenes.
Best Practices for Intrusion Detection
The best practices to follow for a robust intrusion detection are the following:
- How to Optimize IDS Performance:Keep your IDS in top shape by training it regularly, kind of like keeping a watchdog alert with regular walks and challenges.
- Security Recommendations:Stay vigilant, update your defenses, and don't get sloppy. It’s the digital equivalent of locking your doors and checking your windows before bed.
- Regularly Update Signatures :Ensure that the IDS is equipped with the latest signatures to detect recent threats. Automatic updates are preferred to minimize the window of vulnerability.
- Integrate Threat Intelligence ;Incorporate external threat intelligence feeds to enhance detection capabilities and stay informed about the latest threats.
Frequently Asked Questions(FAQs)
What is intrusion detection?
Intrusion detection systems (IDS) monitor networks or systems for suspicious activity that may signal an attack.
Why is intrusion detection important?
IDS helps prevent unauthorized access, data breaches, and disruptions by identifying threats early on.
What are the different types of intrusion detection?
There are two main types: Network IDS (NIDS) monitors network traffic and Host IDS (HIDS) monitors individual devices.
How does intrusion detection work?
IDS uses various methods like signature-based detection (matching known attack patterns) and anomaly-based detection (identifying unusual activity).
What are the limitations of intrusion detection?
IDS can generate false positives and requires ongoing maintenance and updates.
