Introduction
Most WhatsApp SMS blasts don’t get you blocked — misused ones do.
The fear isn’t the method. It’s what people do wrong with it. Businesses assume blasting means spam. However, when done correctly, it’s one of the most effective messaging strategies available.
The method helps you reach hundreds or thousands of users at once — without losing trust or your account. The trick is knowing how to do it safely.
This guide breaks down the right way to run a WhatsApp blast message service. And how to do it smartly, using a trusted tool built for compliance.
What is a WhatsApp SMS Blast?
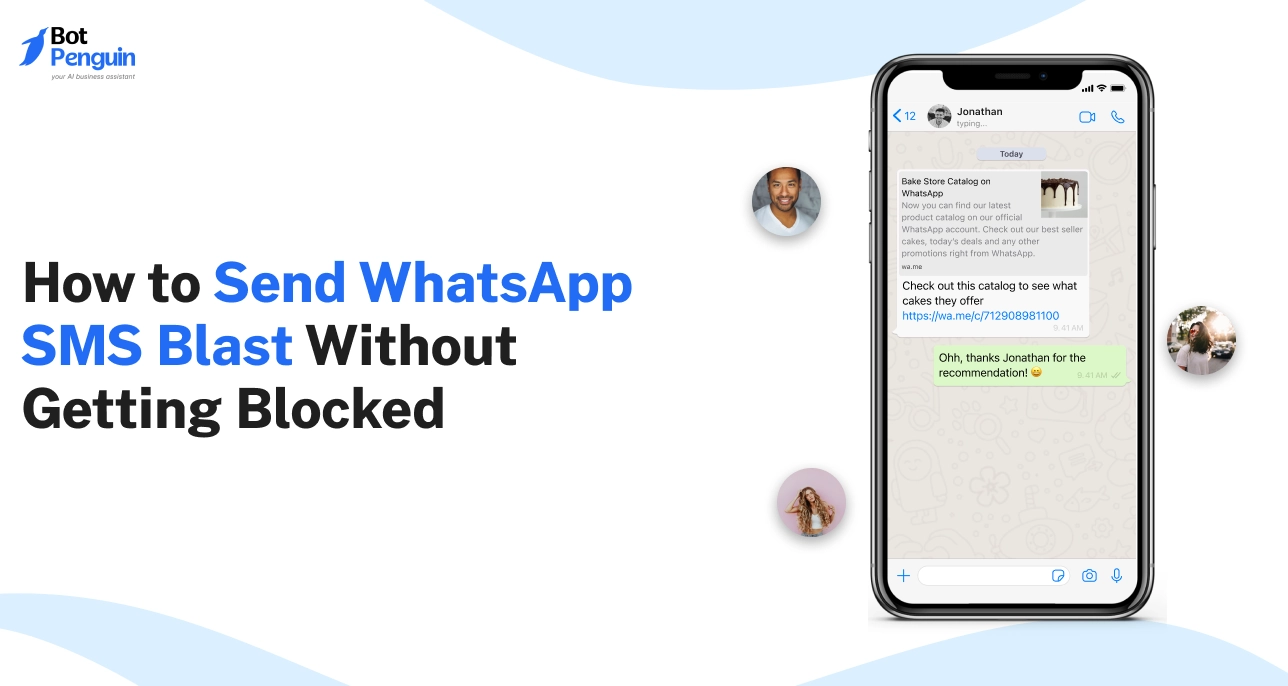
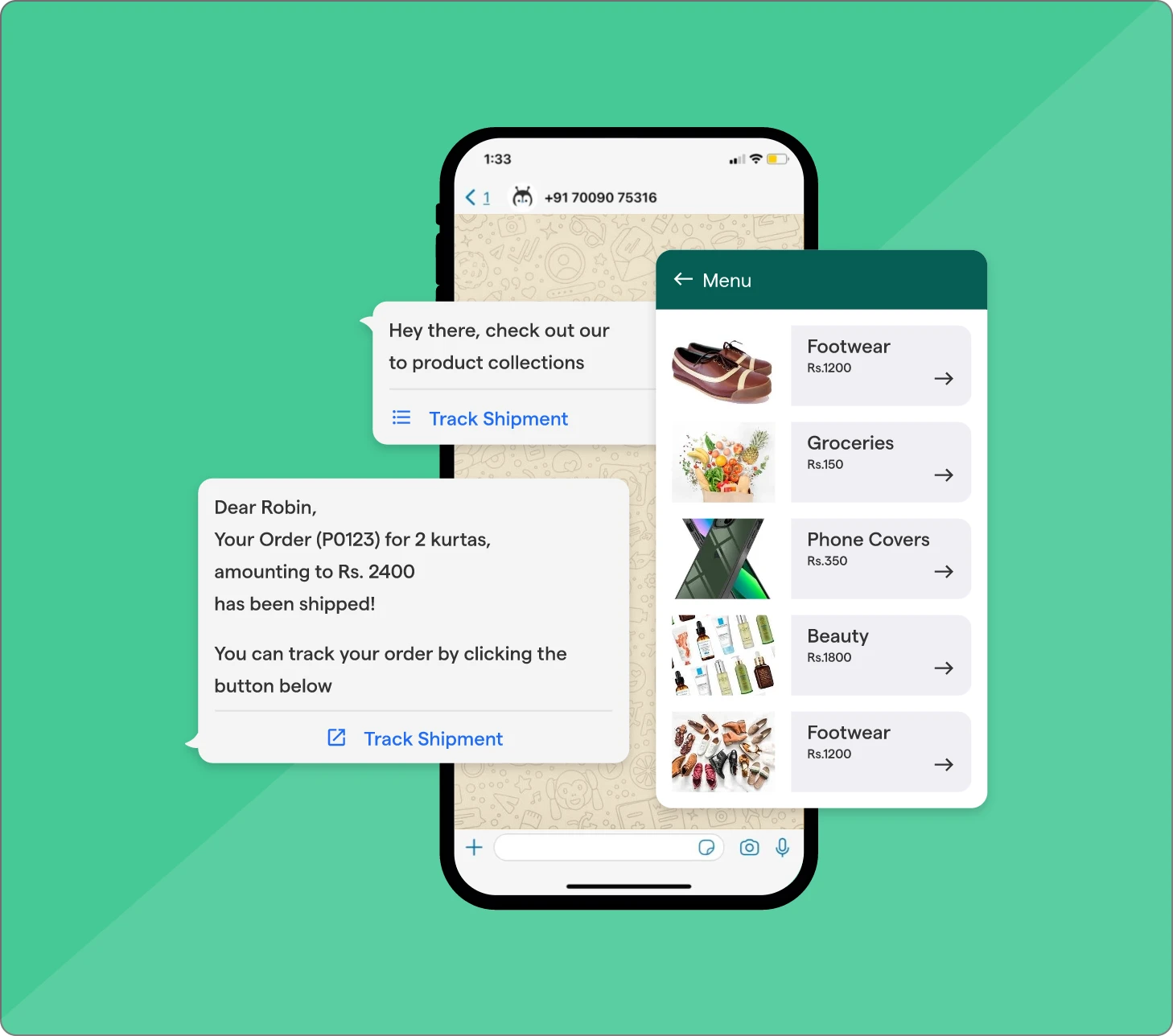
A WhatsApp SMS blast is a way to send the same message to many people at once — without creating a group. It’s a form of one-to-one communication delivered at scale, where each recipient receives the message in their private chat.
When shared with users who have willingly provided their number, it becomes a simple and effective way to stay in touch. It’s not spam — it’s structured outreach that keeps communication clean and direct.
Businesses across industries use it every day to send order updates, appointment reminders, promotions, announcements, and more — all without triggering complaints or blocks.
Imagine a local salon running a weekend offer. Instead of calling each customer, they send one message that reaches everyone individually. No group threads. No reply-all noise. Just a private message that feels intentional and personal.
The best part? If the user replies, it opens as a regular chat — making it easy to continue the conversation without disruption.
Behind the Scenes: How It Works
Now, while the message feels personal to each user, you’re not manually sending it to everyone.
This is where a WhatsApp SMS blaster comes in. It’s a tool that helps you send the same message to hundreds of contacts individually — without creating groups or using the broadcast feature. The idea is simple: you upload a list, write your message, and the tool sends it one by one, just like a human would.
To avoid raising flags, the blaster adds slight delays between messages and spreads them out over time. This helps maintain a natural delivery flow and reduces the chances of your number getting blocked.
Many of these tools also clean up contact lists, remove invalid numbers, and ensure correct formatting — making the process smooth from start to finish.
What you get is a simple workflow: fast, consistent delivery without needing to open dozens of chats.
That’s what makes WhatsApp blasting so effective. It’s fast. It scales. And it still feels personal.
You’re not flooding inboxes. You’re showing up where your users already are — with messages that feel intentional. And when those messages actually get opened, read, and replied to?
That’s when it stops being just another tool… and starts becoming a real marketing edge; let’s see how!
Why Marketers Prefer WhatsApp SMS Blast
Inboxes are crowded. Ads get ignored. But messages on WhatsApp? They get opened.
That’s precisely why marketers are leaning into it. A well-timed message sent to the right user — in a place they check constantly — changes how brands connect.
It’s no longer about reaching more people. It’s about being seen, read, and responded to.
Here’s what makes it such a powerful move.
Strong Engagement Metrics
No one checks their SMS inbox or email as often as they check WhatsApp. That’s why campaigns sent via WhatsApp blast marketing often see open rates above 90%, with click-throughs and replies happening within minutes.
For example, a clothing store announcing a flash sale can expect far faster traction through WhatsApp than through email.
The message doesn’t sit unopened — it shows up where the user chats daily. And since the format is conversational, users are more likely to respond or take action.
In short, it gets noticed — and acted on.
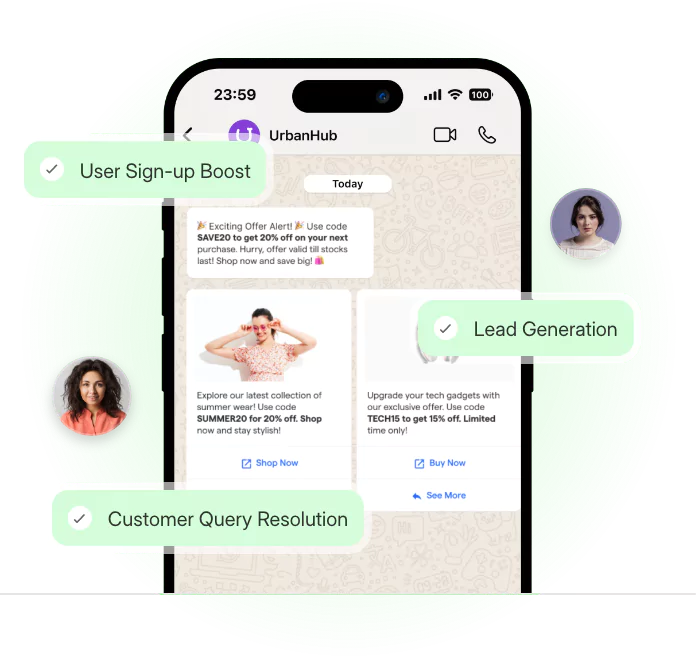
Advanced Targeting Capabilities
What makes blasting truly valuable is the ability to send the right message to the right person.
Modern tools, including WhatsApp blast providers, allow marketers to segment users by location, behavior, or interest. That means a gym owner can send membership reminders only to inactive users, while sending promotions to first-timers — all in one go.
This level of targeting not only improves results but also lowers the risk of your messages being ignored or marked as irrelevant.
The more tailored the message, the more natural it feels — and the less it feels like a blast at all.
Cost Benefits for Small Businesses
Running large-scale SMS campaigns or paid ad promotions can get expensive fast. But with a proper WhatsApp blast message service, you can reach a high volume of users without high costs.
For small businesses with limited budgets — like local retailers or service providers — this makes a real difference. You can communicate with hundreds of customers using a tool that’s both affordable and efficient.
And since the replies come back as individual messages, it also saves time on back-and-forth coordination.
So, whether it’s reach, targeting, or budget — marketers have plenty of reasons to pick WhatsApp.
But does that mean it’s risk-free? Let’s explore.
Is WhatsApp SMS Blasting Legal and Safe?
Many businesses hesitate to try WhatsApp SMS blast because of fears around getting flagged or banned. And honestly, that hesitation isn’t baseless. It can go wrong when shortcuts are involved.
But the issue isn’t with the method. It’s with how it’s executed.
WhatsApp does allow bulk messaging — under specific conditions. If you follow the rules, blasting becomes not only safe but fully compliant. It all comes down to the platform you use and the practices you follow.
Let’s clear up the confusion.
WhatsApp’s Policy on Bulk Messaging
WhatsApp isn’t against businesses sending messages to multiple users. But it’s strict about how you do it.
Mass messages sent through personal accounts are a clear violation. So are tools that bypass limits or spoof activity. That’s where bans happen.
To stay compliant, businesses must use the Business API or approved tools that follow WhatsApp’s delivery rules. These platforms let you message customers who have opted in — with complete control and visibility.
If you’re using a legitimate WhatsApp blast message service, you’re playing within WhatsApp’s own system — not breaking it.
That’s the difference between getting flagged and getting results.
Risks of Shady Tools
The biggest threat to your account isn’t the message — it’s the tool you use to send it.
Free or unverified software often promises “unlimited” messaging. But behind the scenes, they send messages too fast, ignore opt-in rules, or fake delivery behavior. WhatsApp flags these patterns quickly.
It only takes a few minutes of misuse for your number to be restricted — or worse, permanently banned.
That’s why choosing a trusted WhatsApp SMS blaster matters. A good tool won’t just send your messages. It’ll protect your account while doing it.
And that’s a non-negotiable.
Using the Right Platform Makes The Difference
Everything changes when you use the right platform.
A safe, compliant tool ensures your messages go out correctly — with pacing, contact checks, and response handling built in.
This is where a platform like BotPenguin comes in.
It’s designed to help businesses send structured, rule-abiding campaigns at scale. It doesn’t just automate. It keeps your account within WhatsApp’s safe zone — while still letting you connect with hundreds of users at once.
And since it works with opt-in contacts only, your outreach remains clean, targeted, and compliant with policy.
Now, we’ll take a closer look at how BotPenguin handles all of this — and why it’s built for safe, effective WhatsApp blasting.
Why Use BotPenguin for WhatsApp SMS Blasts
Nothing says safe like choosing the right foundation.
WhatsApp messaging can be powerful—but only if your tool keeps you compliant and effective at the same time. BotPenguin fits both bills.
It offers automation, personalization, and compliance—all bundled into one platform made for businesses aiming to connect, not get blocked.
Here’s why it stands out.
Powerful Features Built for Marketing
BotPenguin offers everything marketers need in one clear interface.
You can design drip campaigns and automated response flows—no coding necessary. Add media, quick replies, and templates to make each message engaging.
The platform also features a unified inbox and content-rich message templates, making interactions feel personal and valuable.
There’s real-time analytics to track opens, responses, and chat volume so you can optimize next steps.
Additionally, it supports SMS-style message automation, order alerts, reminders, and conversational flows—all from a single dashboard.
Built for All Business Sizes
Running solo or growing fast? BotPenguin adapts to your scale.
Its drag‑and‑drop bot builder is intuitive—even for non-tech users. Start risk-free with the Free Forever plan that requires no credit card.
As messaging needs expand, you can upgrade to get CRM integrations, expanded automation, and higher usage limits.
Setup stays simple while features grow—no fuss, no forced migration.
Transparent Pricing, No Spam Risk
BotPenguin values clarity as much as compliance. Its pricing is transparent and based on conversation volume—no hidden charges or inflated markups.
More importantly, it utilizes WhatsApp API-approved frameworks and templates, ensuring your campaigns remain clean and spam-free. There’s zero reliance on sketchy tools or loopholes.
With BotPenguin, what you see is what you get: trusted messaging that stays within the rules and protects your account.
BotPenguin isn’t just a mailing tool. It’s a safe, full-featured system built to help your WhatsApp campaigns be both practical and compliant.
And now that you know what it can do, let’s walk through how actually to use it to send your first campaign.
How to Send WhatsApp SMS Blast Using BotPenguin
BotPenguin is one of the safest and most powerful tools for sending WhatsApp SMS blasts. So, let's learn to launch your own campaign—without risking blocks or dropping misses.
This walkthrough will guide you through every step, from account setup to analyzing your results.
We’ll show you how to keep outreach targeted, compliant, and effective. Before you know it, you'll be delivering messages that are timely, personal, and strategic—exactly how they should be.
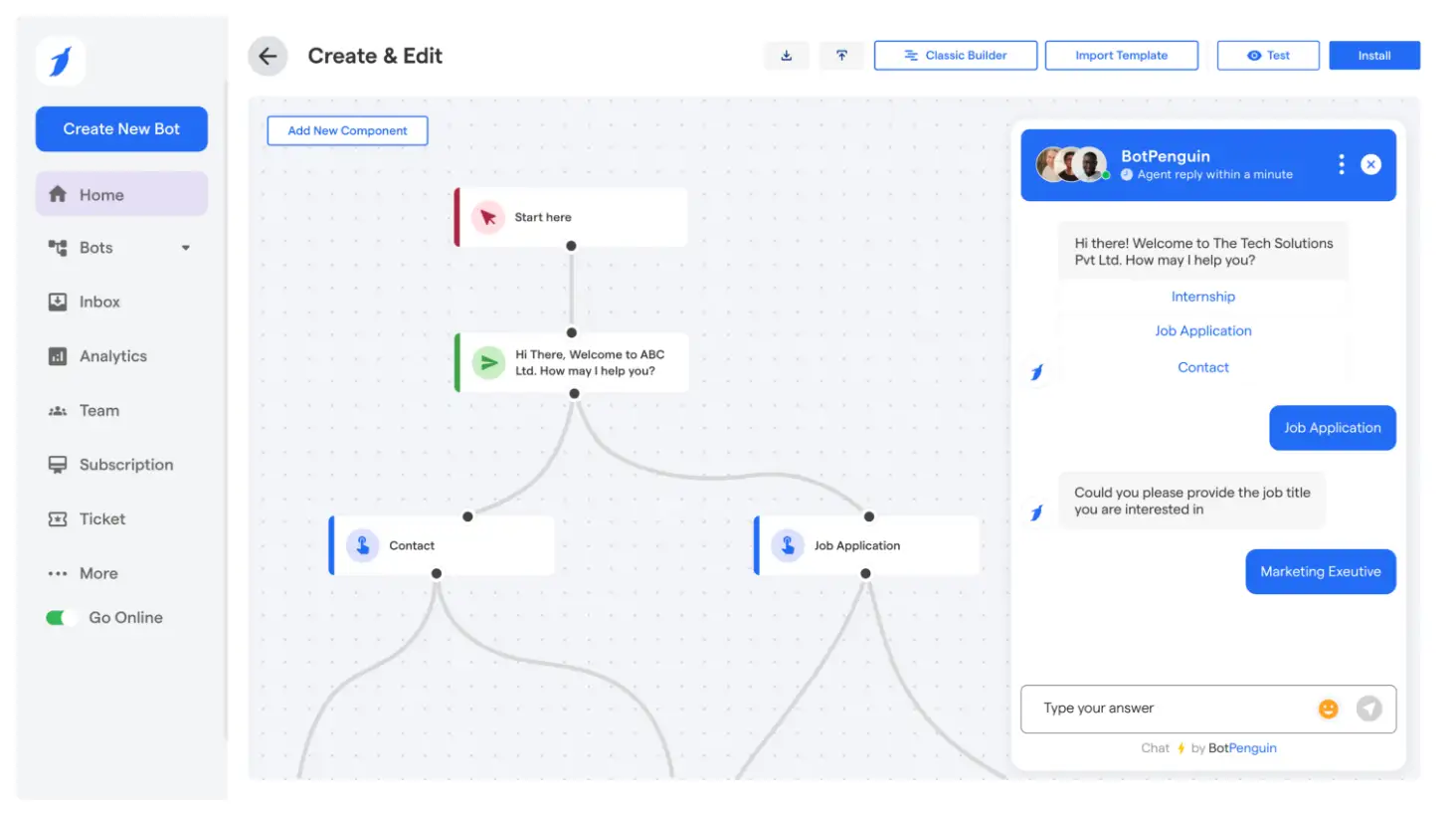
Step 1 – Sign Up and Access the Dashboard
Start by registering for a BotPenguin account.
The sign-up is straightforward, and you'll be directed to a clean, intuitive dashboard right away.
Click on “Create Bot” and select WhatsApp as your channel. Then link your WhatsApp Business Account or Meta Business Manager to ensure you're using the official API.
The interface is beginner-friendly and straightforward—no hidden menus or confusing jargon. Even if you're new to WhatsApp automation, you'll be ready to build your first blast in minutes.
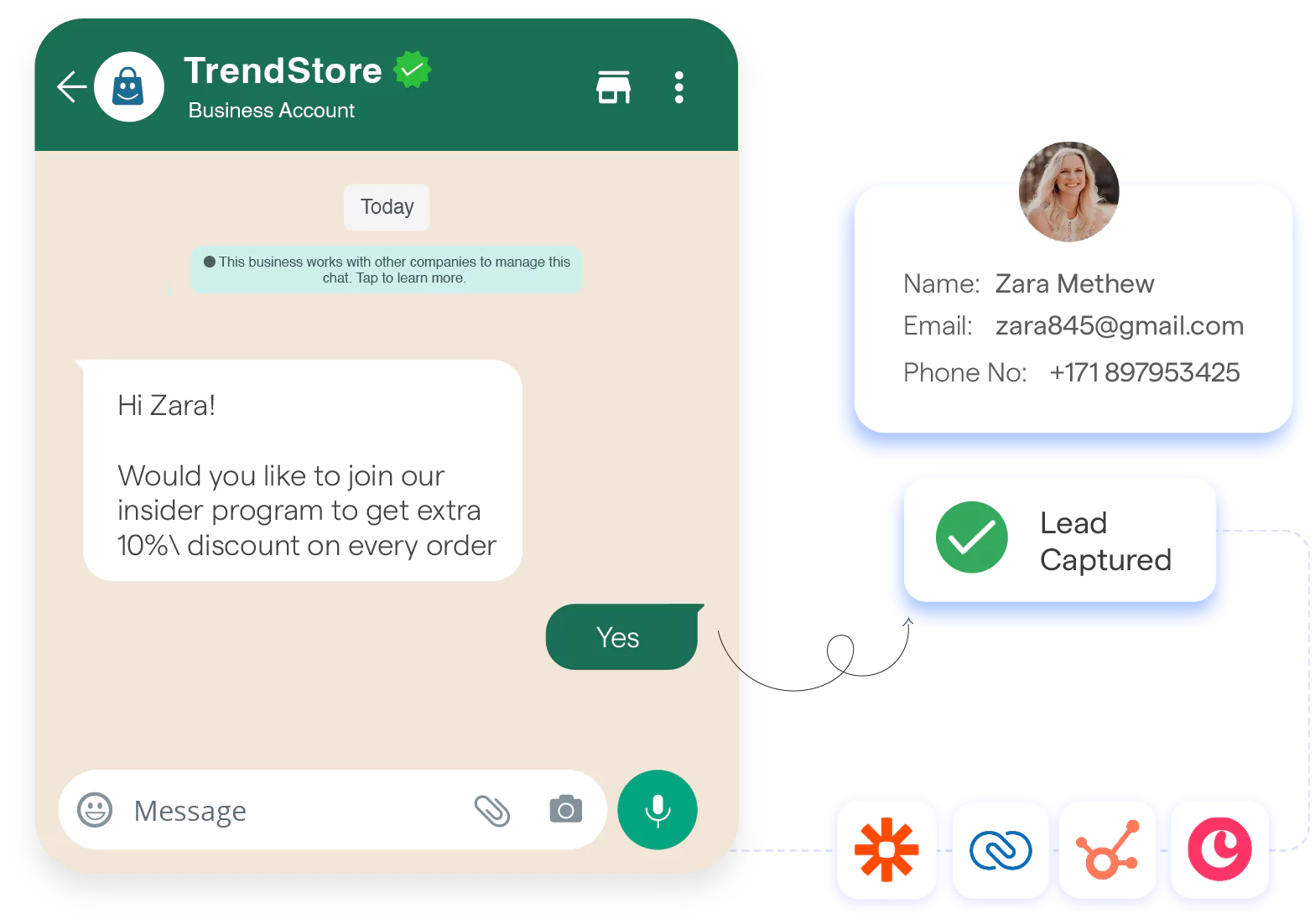
Step 2 – Upload Verified Contact List
Next, upload your contact list using BotPenguin’s contact tools or API.
Always confirm that each number is formatted correctly (including country code) and that the user has explicitly opted in. Adding tags or custom fields helps segment users—for example, “orders pending,” “loyal buyers,” or "appointments pending."
Clean data, properly segmented, ensures your message is relevant and stays complaint-free.
Step 3 – Compose and Personalize Your Message
Use the visual flow builder to craft your message. Keep it short, clear, and action-focused.
Avoid spammy language like “BUY NOW!” Instead, say something useful like: “Hey Alex, your prescription is ready. Reply with YES for pickup.”
You can add personalized tags (e.g., {name}), quick replies, or images to boost engagement. This keeps conversations feeling human and relevant.
Step 4 – Schedule or Send Immediately
Decide when you want your message to go out. Use BotPenguin’s scheduler to pick the perfect time—like an hour before a class or a reminder just in time.
Scheduling helps avoid odd-hour sends and boosts response rates. The platform handles messaging in smart intervals to prevent triggering spam filters.
Whether you choose immediate send or timed blast, the system balances speed with caution.
Step 5 – Track and Improve
After your message goes out, head to the analytics dashboard.
You’ll see delivery status, open/read metrics, and user responses. Watch how certain segments respond more, or notice better engagement at certain times of day.
Use this feedback to sharpen your next blast—tweaking tone, timing, or audience. Over time, your messaging becomes more effective and refined.
You’ve just seen how easily you can set up a powerful WhatsApp SMS blast campaign. By using BotPenguin and following these steps, you’ve minimized risks and maximized efficiency.
Now, the final piece of the puzzle: learning how to maintain a good standing account over the long term.
Best Practices to Avoid Getting Blocked
Just because you can send messages doesn’t mean you should send them without a plan.
A successful blast campaign doesn’t rely on speed or volume — it’s all about timing, relevance, and value. If you send messages too frequently or use low-quality content, you risk being blocked by users or flagged by WhatsApp.
With the right habits, especially when using a compliant WhatsApp blasting service like BotPenguin, you can consistently run safe and high-performing campaigns.
Here’s how to avoid trouble.
Make Messages Value-First
No one likes spam — not even your most loyal customers. That’s why your WhatsApp blast marketing should always prioritize value.
Instead of pushing constant promotions, try sending content that actually helps. Think: delivery updates, appointment confirmations, important announcements, or real-time support follow-ups. These keep your audience engaged and less likely to block you.
Even when you’re promoting an offer, make it relevant. A deal that matches past purchases or location-based alerts will always perform better than a random sale.
The more useful your message, the more welcome it feels — that’s the key to sustainable outreach.
Don’t Overblast
Frequency is where many businesses go wrong.
Even if you’re running a great WhatsApp blasting service, sending too many messages in a short span can irritate users and trigger blocks.
A safe rhythm is one to two messages per week. This keeps your brand top of mind without being overwhelming.
Think of your message as a gentle nudge, not a constant tap on the shoulder. If every ping feels like a promotion, people will eventually silence or report you.
Focus on consistency, not volume. That’s where long-term engagement lives.
Segment for Relevance
One message doesn’t fit all.
BotPenguin helps you run a smarter blast campaign by letting you tag and segment users. You can create lists based on behavior, purchase history, engagement, or interest level.
This means your message goes to the right people at the right time — no wasted impressions.
For example, someone who just signed up might get a welcome message. A returning buyer could get an exclusive deal. And inactive users might receive a re-engagement nudge.
Segmenting improves open rates and reduces complaints. It also shows your users you know them — and respect their inbox.
Following these simple practices makes all the difference. You avoid bans, improve results, and make every blast count. And when you power this approach with BotPenguin, safety and performance go hand in hand — setting you up for the next big win.
Let’s take a look at how real businesses are already using it in action.
Real-World Use Cases: Powered by BotPenguin
Best practices only matter when they work in the real world. And they do.
Businesses across industries are already running safe, high-performance campaigns using BotPenguin.
From improving engagement to reducing manual workload — these use cases demonstrate how a WhatsApp SMS blast can deliver real value when executed effectively.
Let’s break it down by industry.
1. eCommerce
In eCommerce, timing is everything.
Online stores use BotPenguin to send instant flash sale alerts, price drop notifications, and stock refill messages — all through automated WhatsApp blast marketing.
Cart abandonment is another big win. If a user leaves something behind, they get a quick nudge with their exact cart details and a clickable link. It feels personal, not pushy.
You can also keep customers updated on order status or delivery changes without human involvement.
It’s not about flooding inboxes — it’s about showing up when it matters. BotPenguin makes that process efficient and human.
2. Healthcare
For healthcare providers, clear communication builds trust.
Clinics and hospitals use BotPenguin to confirm appointments, remind patients of upcoming checkups, and send out awareness messages during health campaigns.
Instead of long queues or missed follow-ups, patients receive updates directly in their WhatsApp chat — no login or email needed.
For example, a dental clinic could send a 6-month reminder for a cleaning. A pediatrician might send vaccine alerts.
The WhatsApp SMS blast here becomes a life-improving utility, not just a tool — and BotPenguin ensures these critical touchpoints are timely, relevant, and secure.
3. Education & Coaching
Schools, colleges, and coaching centers use BotPenguin to reach students where they actually check messages — on WhatsApp.
Need to remind them of an upcoming test? Change in class timing? Promote a new enrollment batch? Everything can be done with just a few clicks.
It’s also great for parent-teacher communication, especially when sending fee reminders or important school notices.
Blasting isn’t spam in this context — it’s structure. And that’s why WhatsApp blast marketing is proving so powerful in education.
4. Local Businesses
From salons to auto repair shops, local businesses thrive on repeat customers.
BotPenguin helps them send discounts, confirm bookings, and ask for feedback — all without needing a separate marketing team.
A salon can blast a weekend deal. A mechanic can confirm next-day appointments. A bakery can alert regulars when a popular item is back in stock.
Each message lands privately, looks clean, and opens a 1:1 chat if the user replies. That's what makes the WhatsApp blast service both personal and scalable.
These examples aren’t edge cases. They’re everyday wins powered by BotPenguin’s reliable automation, intelligent segmentation, and user-friendly design.
Conclusion
What started as a misunderstood term is now a proven growth strategy — when handled responsibly. A WhatsApp SMS blast isn’t spam. It’s timely, 1-to-1 communication that keeps users informed, engaged, and happy.
From segmenting your audience to personalizing each message, every step matters. And when paired with a compliant, reliable WhatsApp blast service like BotPenguin, blasting becomes both safe and effective.
So if you’ve been hesitant, now’s the time to rethink.
Explore BotPenguin and start sending smarter messages — the right way.
👉 Try BotPenguin Today!
Frequently Asked Questions (FAQs)
Can I send a WhatsApp SMS blast using multiple phone numbers to bypass limits?
Technically, yes — but it's risky. WhatsApp may detect unusual sending behavior and flag all associated numbers.
It’s better to use an official tool like BotPenguin that respects platform limits and ensures deliverability without shortcuts.
How do I know if a contact has opted in to receive WhatsApp messages?
Opt-ins can be collected via checkboxes on forms, explicit chat initiations, or consent-driven WhatsApp buttons.
You should always store proof of consent, as WhatsApp may ask for it in case of compliance checks.
What’s the difference between using a regular WhatsApp number vs. a Business API number for blasts?
Regular numbers aren't designed for automation and can easily get flagged. WhatsApp Business API numbers are built for large-scale, structured communication — and are the only compliant way to send automated bulk messages.
Can users report my business even after opting in for messages?
Yes, and WhatsApp may still review those complaints. This is why it’s essential to send value-first content and allow easy opt-outs.
High report rates — even with consent — can impact your sender reputation.
How can I make sure my blast messages don’t sound robotic or templated?
Use personalization tags, varied sentence structures, and human-like copy. Avoid overusing marketing buzzwords.
A conversational tone paired with useful content makes your blast feel like a real message, not a bot spam.
Will WhatsApp notify me if my account is at risk of being blocked?
Not always. Sometimes, the number is flagged or restricted without prior notice. However, consistent quality messaging and low complaint rates help maintain a healthy sender profile and avoid such penalties.
Can I resend a blast to people who didn’t open the first message?
Yes, but with caution. Avoid sending the same message again. Instead, reframe the content or offer a different angle. Re-blasting should be occasional and always value-driven to prevent user fatigue.