Introduction
Are you afraid of losing sensitive customer data like names, emails, credit cards, SSNs, etc.?
With over 2.5 quintillion bytes generated daily and cybercrime striking a business every 40 seconds, data security emerges as the protective seat belt keeping organizations and consumers safe.
Recent years bore witness to blockbuster breaches from Yahoo’s 3 billion records compromised to the SolarWinds supply chain debacle. 2021 saw ransomware attacks surge 105% with average payment demands doubling to $220,298.
The message is clear – inadequate data security today wreaks havoc. Yet despite the risks, many still don't understand the importance of data security.
Only 48% of businesses have an incident response plan and barely 50% provide data security training, per a 2022 DataProt survey.
In the high-stakes race toward digital innovation, organizations must buckle up with defense-in-depth security, staff training, and robust incident plans. For consumers, vigilance and digital hygiene like strong passwords remain key.
By recognizing the importance of data security in digital progress, let's find out more about why data security matters in this blog.
What is Data Security?
Data security refers to the protection of all information stored and transmitted digitally. It encompasses the processes, policies, and cybersecurity tools implemented to prevent unauthorized access, exposure, or loss of sensitive data.
Effective data security safeguards data integrity and privacy through access controls, encryption, backups, network protections, and physical security.
Robust data security measures provide layers of defense against threats both internal and external.
Well-designed data security enables organizations to securely manage information, comply with regulations. It ensures business continuity, and maintains the trust of customers.
Ultimately, data security relies on protecting the confidentiality, integrity, and availability of data from compromise, disruption, or misuse. Implementing comprehensive data security is essential for managing risk and allowing organizations to fully leverage data in today's digital landscape.
Along with Data Security, BotPenguin has other features too such as-
- Marketing Automation
- WhatsApp Automation
- Customer Support
- Lead Generation
- Facebook Automation
- Appointment Booking
Why Does Data Security Matter?
Now that we understand the what, let's explore the why behind data security.
Protects sensitive information
Effective data security prevents unauthorized access and exposure of proprietary information, customer data, intellectual property, or other sensitive assets. This safeguards an organization's sensitive information
Maintains compliance
Data security ensures adherence to regulatory compliance mandates around consumer privacy, financial data, healthcare records, and more. Non-compliance exposes organizations to major fines and reputational damage.
Builds customer trust
Consumers expect their data to be handled securely. Robust data security sustains customer confidence and loyalty to the brand.
Enables business continuity
Secure data allows organizations to reliably access information needed for operations. Outages have costly cascading business impacts.
Manages reputational risks
Breaches harm the brand reputation and customer retention. Solid data security reduces this risk complex.
Drives competitive advantage
With robust protections, companies can securely leverage data for smarter decisions, better products, and strategic initiatives.
Who Needs Data Security?
Data security is a universal need. In this section, we'll explore the importance of data security for individuals, businesses of all sizes, and even government organizations.
Importance of Data Security for Individuals
Whether you're tech-savvy or technologically challenged, your data matters. Robust digital practice around device usage, passwords, and sharing of information is critical for individuals. It protects their privacy, finances, and their families.
Data Security Measures for Small, Medium, and Large Businesses
In the corporate landscape, data security measures are very important. Small, medium, or large - every business holds valuable data that needs protection. The key is matching data security measures with the level of risk and resources at each stage of business growth.
Data Security Regulations in Government and Public Organizations
Government and public organizations handle a treasure trove of sensitive data. Data protection must be a top-level priority with coordination across all stakeholders in government. Public and employee trust hinges on robust strategies tailored to the unique role and risks of securing public data.
How to Implement Data Security Regulations?
Here is how an organizations can take to implement effective data security measures:
Assess Your Data Vulnerabilities
Start by identifying potential weaknesses in your data infrastructure. Conduct a thorough audit to understand the types of data you store, where it resides, and who has access to it.
Define Access Controls
Set up role-based access controls (RBAC) to determine who can access specific data. Limiting access to authorized personnel ensures that sensitive information is only available to those who truly need it.
Educate Your Team
Data security is a team effort! Educate your employees about data protection best practices, the importance of strong passwords, and how to recognize phishing attempts.
Best Practices for Data Protection
Now that you've laid the foundation for your data security strategy, let's explore some best practices to fortify your defenses:
Encryption: Safeguarding Data in Transit and at Rest
Encrypting your data is like putting it in an impenetrable lockbox. Use encryption protocols to protect data both while it's moving between systems and while it's stored in databases.
Multi-Factor Authentication: Strengthening Access Controls
By requiring users to provide multiple forms of verification (e.g., password and fingerprint), you reduce the risk of unauthorized access.
Data Security Regulations and Compliance
Data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), are designed to safeguard user privacy and control how data is collected and used.
Data Security in Cloud Computing
Cloud Computing introduces new challenges in terms of data security. Cloud data security brings its own set of risks. It includes data breaches, unauthorized access, and potential data loss. Understanding these risks is crucial for effective protection.
Cybersecurity Training and Awareness
In the battle against data breaches, your employees are your first line of defense. Empowering them with cybersecurity knowledge is paramount. Educating employees about data security threats, best practices, and their responsibilities can significantly reduce the risk of breaches.
Make cybersecurity a part of your organization's DNA. Fostering a culture of awareness and vigilance can fortify your defenses.
Incident Response and Disaster Recovery
Despite our best efforts, breaches can still occur. Being prepared for such events can make all the difference. Developing a well-thought-out incident response plan ensures a swift and effective response when facing data breaches or cyber-attacks.
In the event of a breach, staying composed and following a predefined set of steps will help mitigate damage and facilitate recovery.
Emerging Threats and Future Trends in Data Security
In the ever-changing landscape of cybersecurity, new challenges, and risks continue to emerge. Let's dive into some of the latest trends and potential threats that we need to stay ahead of.
Exploring New Cybersecurity Risks
It's crucial to be aware of the following emerging threats:
- Social Engineering in the Digital Age: Cyber attackers are getting smarter in manipulating human psychology to gain unauthorized access to sensitive information.
- Cloud Vulnerabilities: As businesses increasingly rely on cloud services, new vulnerabilities, and attack vectors emerge.

The Evolution of Data Security Solutions
The good news is that cybersecurity solutions are evolving too! Innovations and strategies are being developed to combat these emerging threats:
- Artificial Intelligence (AI) in Cybersecurity: AI-driven security tools are being deployed to detect and respond to threats in real-time.
- Blockchain for Enhanced Security: The distributed and immutable nature of blockchain technology is finding applications in securing sensitive data.
Data Security for IoT
The rapid expansion of the Internet of Things (IoT) introduces exciting possibilities, but it also comes with its fair share of risks. Let's explore the challenges and strategies to ensure data security in an IoT-connected world.
Risks and Challenges in an IoT-Connected World
With billions of IoT devices connecting to the internet, the attack surface expands exponentially:
- Inadequate Security Measures: Many IoT devices lack robust security features, making them vulnerable to exploitation.
- Data Privacy Concerns: The vast amount of data collected by IoT devices raises concerns about user privacy and data misuse.
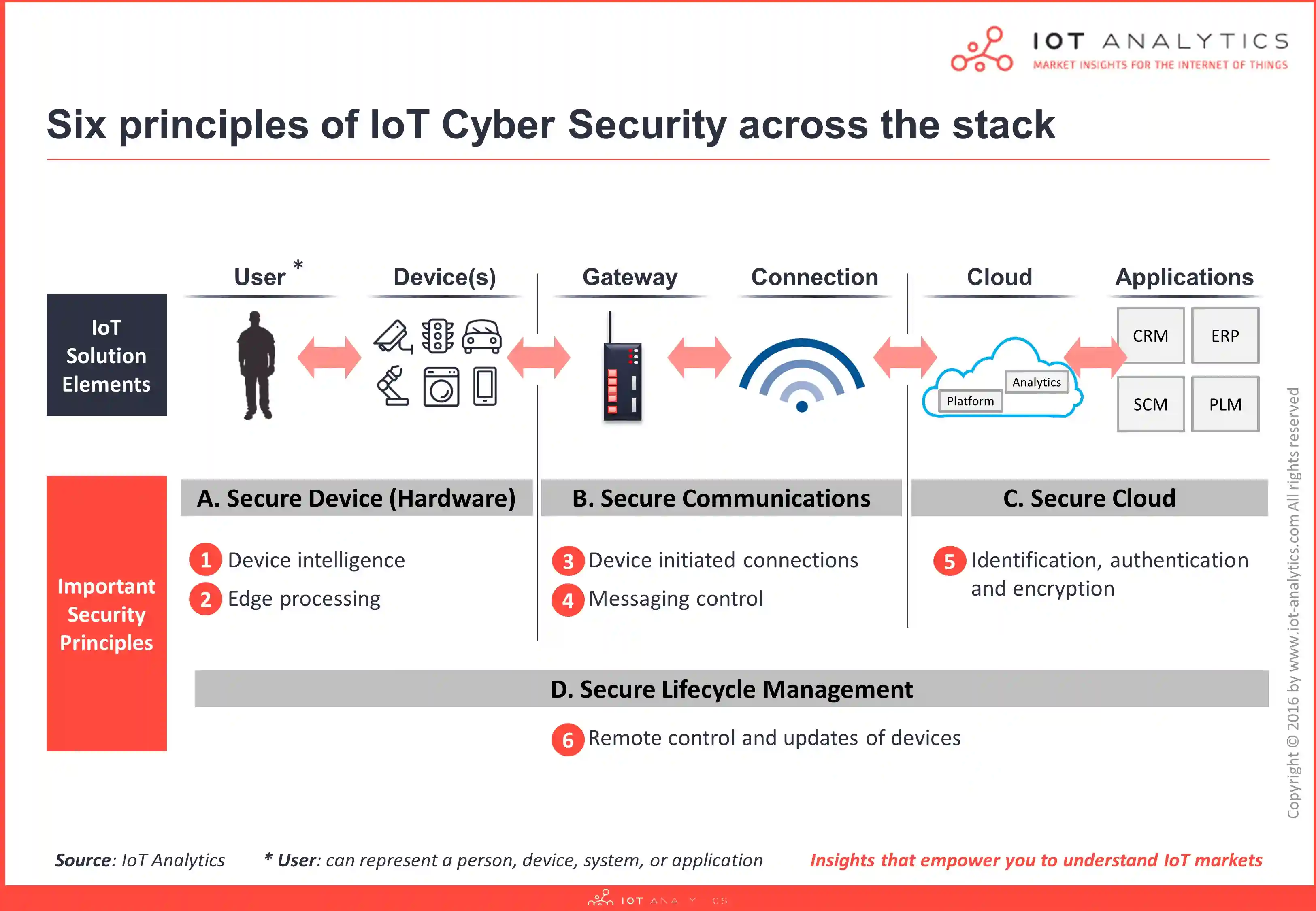
Securing IoT Devices and Networks
To mitigate the risks and ensure a safer IoT environment, the following measures are crucial:
- Strong Authentication and Encryption: Implementing strong authentication and encryption protocols for IoT devices and communication channels.
- Regular Software Updates: Timely software updates and patches to address known vulnerabilities in IoT devices.
- Network Segmentation: Segregating IoT devices into separate networks to minimize the impact of potential breaches.
Conclusion
The importance of data security could not be more in today's ultra-connected digital landscape. As breaches proliferate and cyber threats mount, no organization can afford nonchalance.
A single breach can total a company – average losses now exceed $4.35 million according to IBM’s Cost of a Data Breach Report.
But beyond compliance fears and cost avoidance lies a deeper motivation.
When citizens provide data, they rightfully expect privacy protections and freedom from misuse. When businesses operate online, they require assurance of property and transaction integrity. Only with guarantees of safety does innovation flourish.
Through ongoing training, layered defense, and vigilance powered by breakthroughs like AI, we can collaboratively secure data in motion and at rest. Leadership too must champion data security and demonstrate commitment through planning, investment, and accountability.
In doing so collectively, we can ensure data security.
Frequently Asked Questions(FAQs)
What measures can businesses take to ensure data security?
Data security measures like encryption, access controls, regular data backups, and security awareness training for employees to enhance data security.
How does data security compliance affect businesses?
Data security compliance, such as GDPR or CCPA, is essential for businesses to adhere to legal requirements related to data protection.
What are the common types of cyber threats targeting data security?
Common cyber threats include phishing attacks, ransomware, malware, and social engineering, all of which can compromise data security.
How can individuals protect their data online?
Individuals can protect their data by using strong passwords, enabling two-factor authentication, being cautious of suspicious emails, and avoiding sharing sensitive information on unsecured platforms.
How can data security impact user privacy on digital platforms?
Robust data security practices on digital platforms help maintain user privacy, preventing unauthorized access to personal data and ensuring a safe online experience.
Are there any potential challenges in implementing data security measures?
Implementing data security measures may face challenges such as budget constraints, evolving cyber threats, and ensuring employee compliance with security protocols.